Vulnerability Management
The Vulnerability assessment process comprises the systematic identification of vulnerabilities, along with a comprehensive analysis of their severity, potential impact, and associated risks. In addition, diligent monitoring is in place to track both publicly disclosed vulnerabilities and zero-day threats, ensuring an up-to-date security posture. Prioritization plays a critical role, with vulnerabilities ranked based on their impact, urgency, and patch availability. A strong emphasis is placed on high risk software, where vulnerabilities within vital assets like databases and web servers are isolated and secured, fortifying the overall cybersecurity of the technical infrastructure.
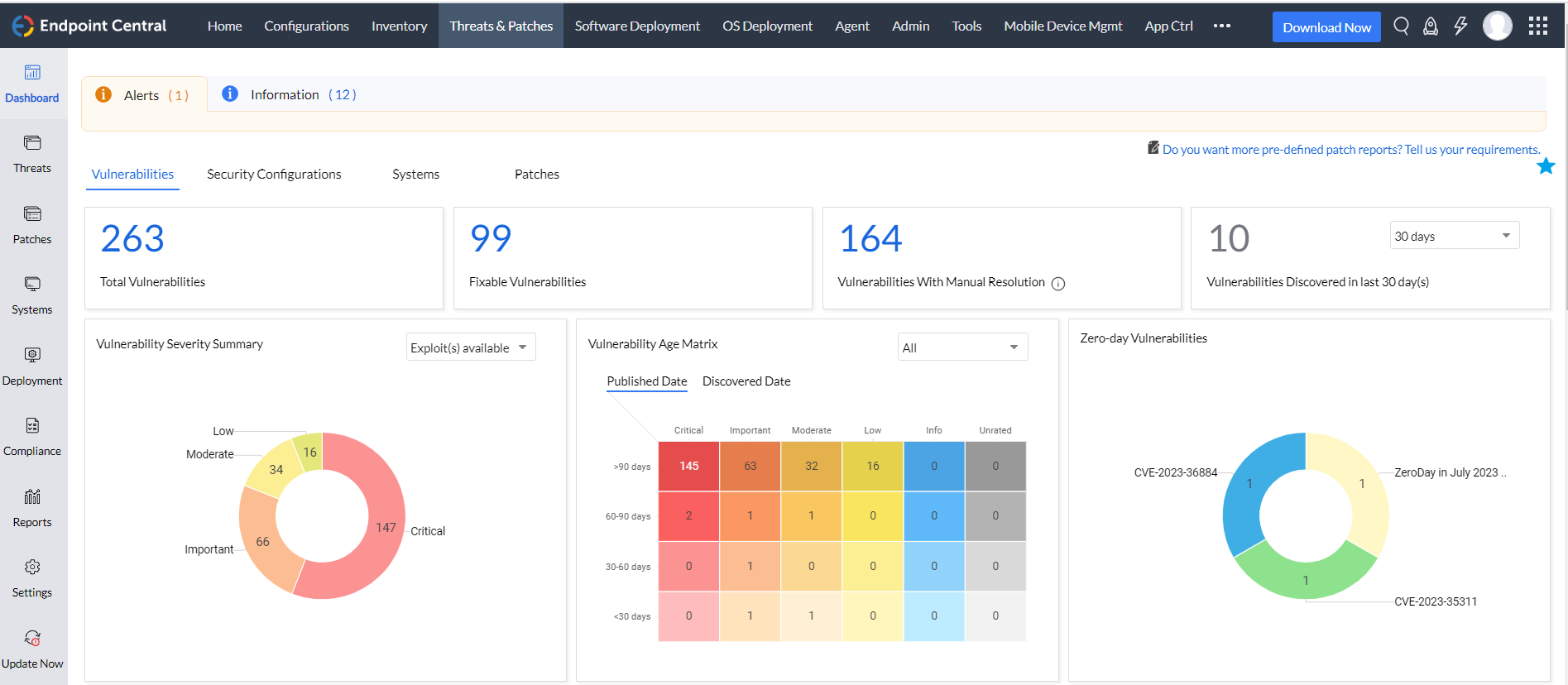
- Zero-day identification: Leverage the capabilities of Endpoint Central to actively monitor and identify zero-day vulnerabilities within your software and system infrastructure. Keep a watchful eye on security advisories and real-time threat intelligence sources, ensuring timely detection.
- Immediate response: Implement a rapid-response plan tailored to zero-day vulnerabilities. This plan includes predefined roles and well-defined procedures to be executed when a confirmed zero-day threat surfaces, allowing for swift and effective counter measures.
- Workarounds and temporary fixes:Utilize the features of Endpoint Central to develop and implement temporary workarounds and mitigation strategies that reduce the risk of exploitation in the absence of available patches. These measures act as a protective shield, safeguarding critical systems and invaluable data until a permanent solution is accessible.
- Continuous monitoring : Maintain continuous vigilance over the status of zero-day vulnerabilities. Stay informed with real-time updates from vendor announcements and security communities to ensure the enduring security of your systems.
- Security configuration management: Configuration Management: Easily identify and correct misconfigurations in operating systems, applications, and browsers, ensuring compliance with security standards.
- Comprehensive auditing: Conduct thorough audits of firewalls, antivirus, and BitLocker status to maintain a secure infrastructure.
- Protection against brute-force attacks: Safeguard your network by enforcing robust password policies and secure logon procedures to prevent brute-force attempts.
- Enhanced security settings: Strengthen your systems with advanced memory protection settings and the retirement of legacy protocols, reducing vulnerabilities and enhancing security without disrupting business operations.
Web Server Hardening
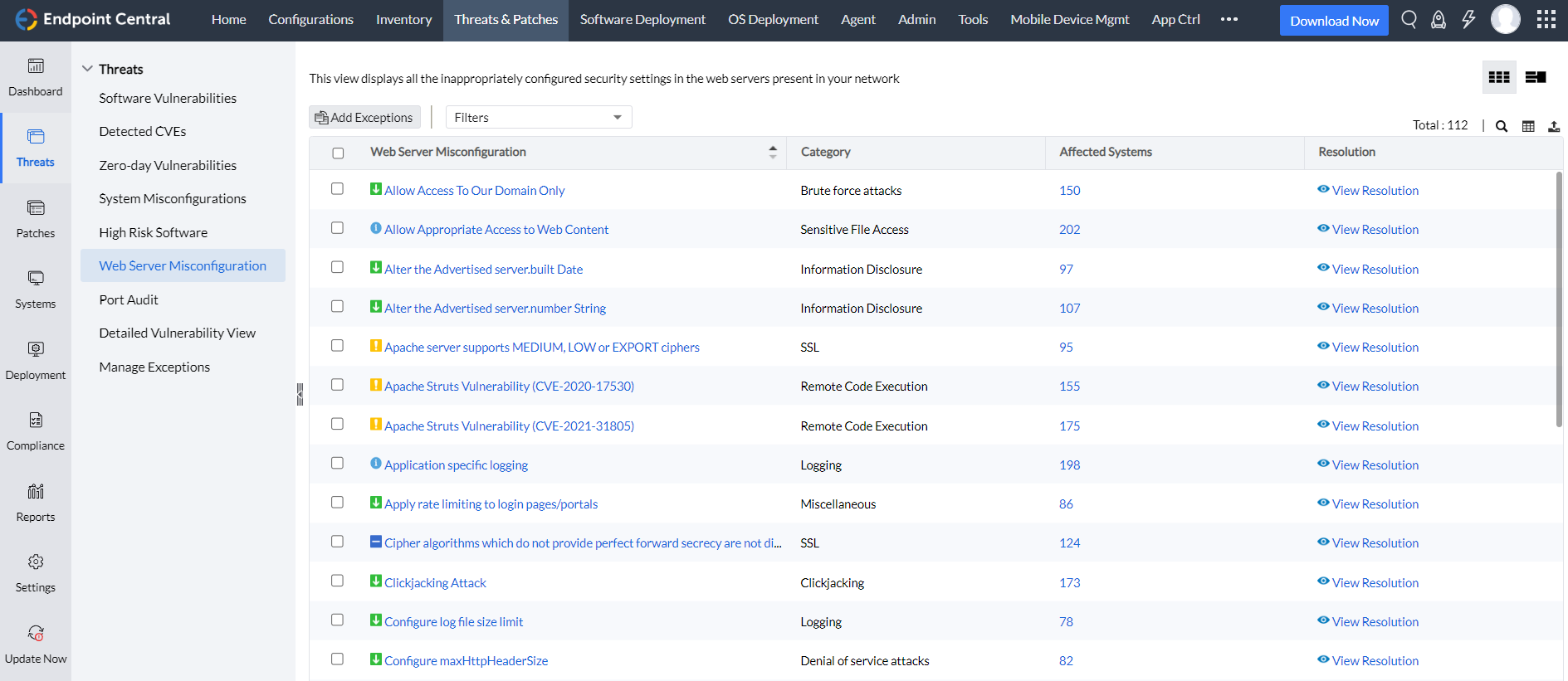
- Proactive configuration monitoring : Benefit from continuous monitoring of your web servers to identify and rectify default and insecure configurations.
- Contextual misconfiguration analysis : Analyze web server misconfigurations with relevant context and receive security recommendations to enhance your server's security posture.
- Secure communication with SSL: Ensure that SSL certificates are correctly configured and HTTPS is enabled, guaranteeing secure and encrypted client-server communication.
- Enhanced Access Control: Verify and enforce restricted permissions on server root directories to prevent unauthorized access and protect your server's integrity.
High-Risk Software Audit
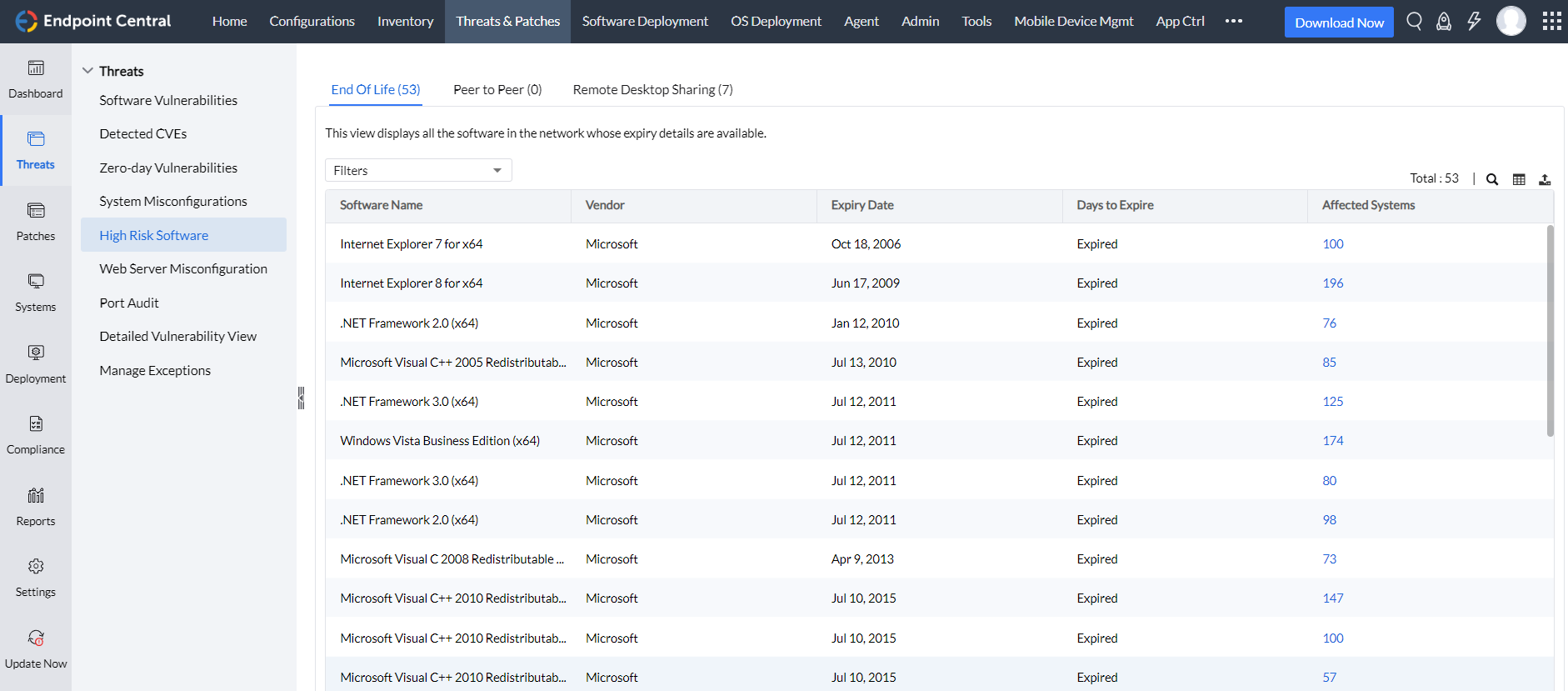
- Legacy software monitoring: Keep a watchful eye on legacy software nearing or already at its end of life, ensuring your systems stay secure and up-to-date.
- Effortless risk mitigation: Access real-time information on unsafe peer-to-peer software and remote sharing tools, and eliminate them with a simple click, bolstering your security instantly.


