Detect anomalous user
and entity behavior with
Log360 UEBA
Identities can be forged, not behavior.
Try Log360Organizations are at a greater risk to cyberattacks and data breaches than ever before. Almost half of all data breaches happening worldwide have an insider element to them. If these threats are not detected and remediated immediately, they can lead to serious consequences.
ManageEngine Log360's UEBA capability is powered by ML algorithms, so it delivers robust and accurate threat detection. It sets a baseline of expected activity for every user and entity, and flags any deviations from that baseline.
Reinforce cybersecurity with Log360 UEBA
Log360 is a unified SIEM solution with anomaly detection capabilities. It uses ML algorithms to analyze patterns of users and other entities in the network. It helps you enforce tighter security measures by detecting behavior anomalies, and strengthens your defenses against insider threats and external attacks. The anomaly detection engine is called Log360 UEBA.
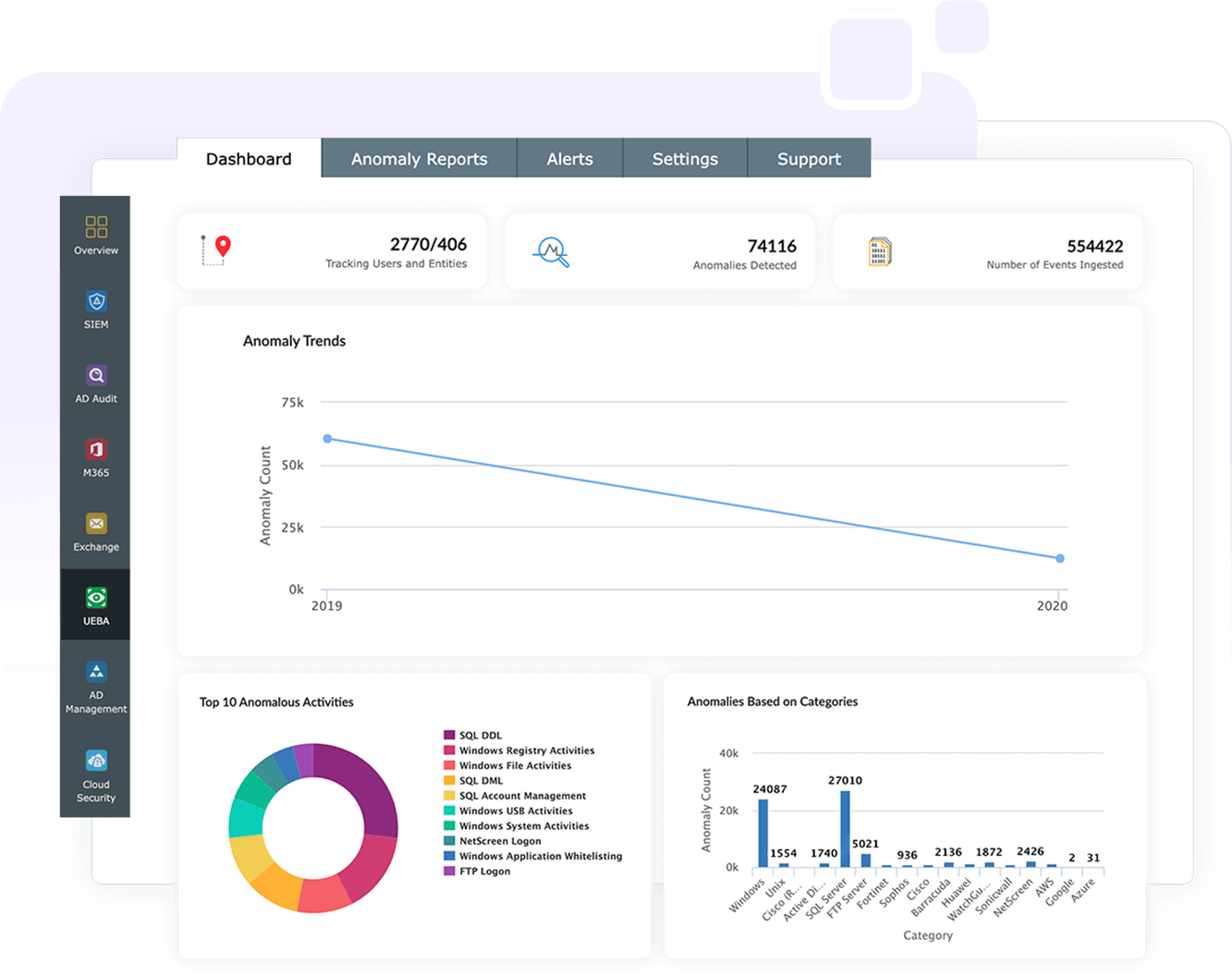
User and entity behavior analytics
Spot deviant user and entity behavior, such as logons at an unusual hour, excessive logon failures, and file deletions from a host that is not generally used by a particular user.
Score-based risk assessment
The Log360 UEBA dashboard gives you greater visibility into threats with its score-based risk assessment for users and entities. This approach helps you determine which threats merit investigation.
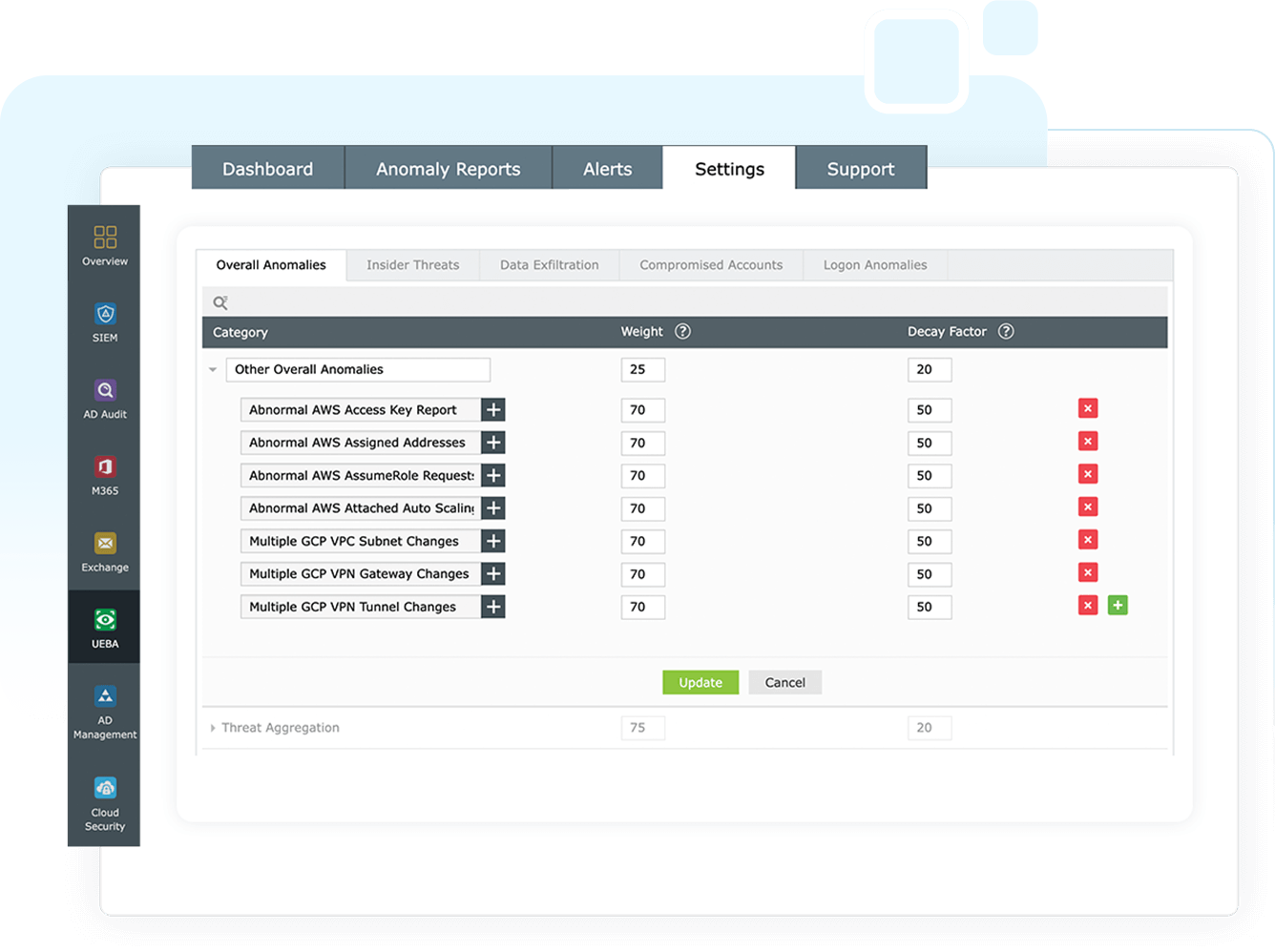
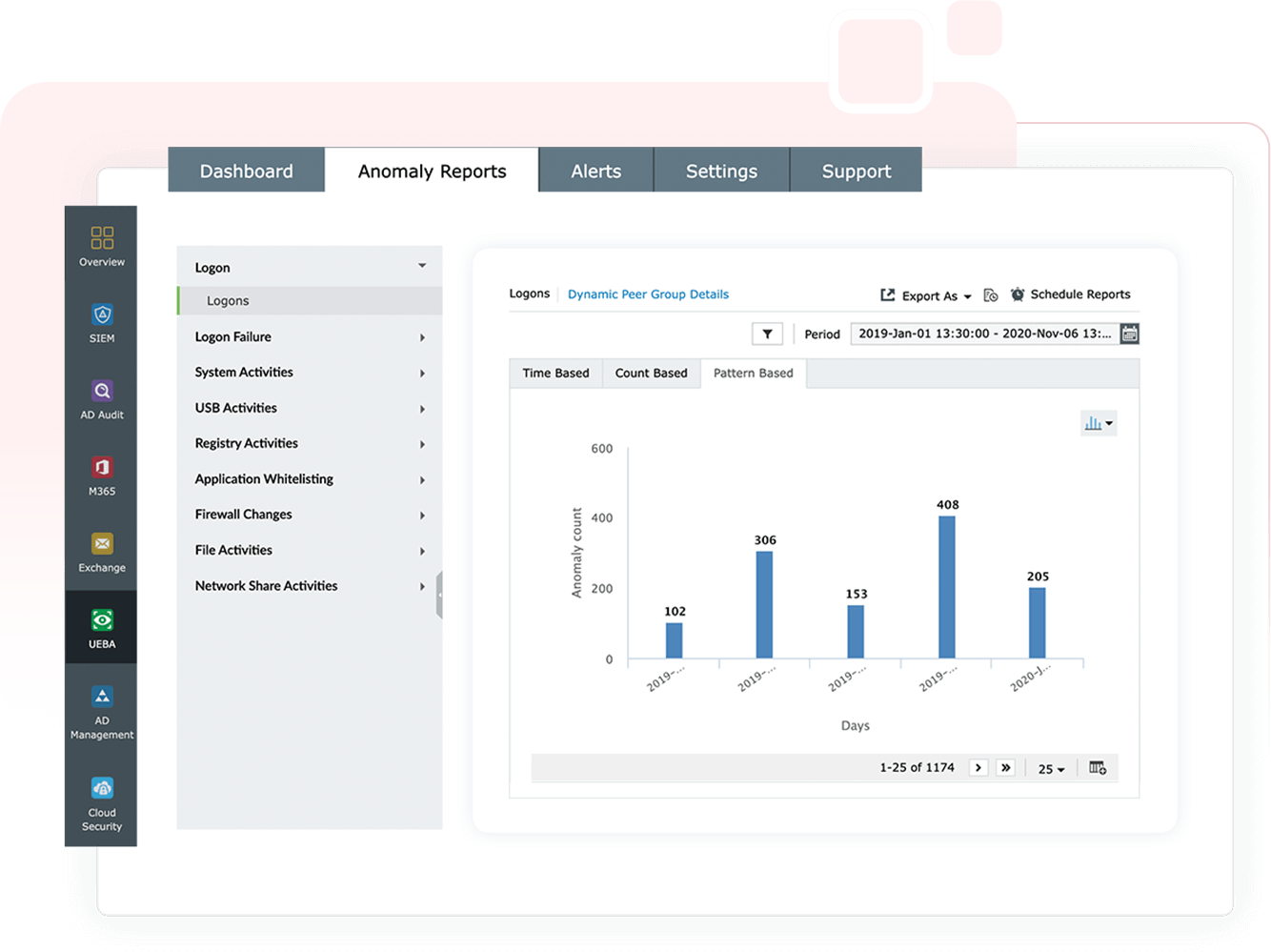
Threat corroboration
Log360 UEBA identifies indicators of compromise (IoC) and attack (IoA), exposing major threats including insider threats, account compromise, logon anomalies, and data exfiltration.
Choose one of three scenarios
With an effective UEBA solution, you can prevent three types of security risks—insider threats, compromised accounts, and data exfiltration. Choose any scenario below to see how UEBA performs in these situations.
Insider
Threat
A malicious engineer tries to sabotage the company.
SteveAn engineer tries to sabotage his company
An engineer named Steve is told that his contract is not being renewed.
Steve is not happy about his termination and wants to exact revenge on his organization.
Know moreAccount
Compromise
A hacker compromises a user account and tries to gain unauthorized access.
bobA hacker compromises a user account
An attacker named John sends a phishing email to Bob.
Bob opens the email and inadvertently starts downloading malware.
Know moreData
Exfiltration
A marketing manager attempts to exfiltrate data from the sales database.
MindyA marketing manager attempts to exfiltrate data
A marketing manager named Mindy decides to leave her organization and join a competitor as a sales director.
She decides to take the customer database with her.
Know moreWatch this video to learn how
UEBA will enable your organization to prevent
insider attacks, account compromise, data exfiltration, and more.
- With
Log360 UEBA, you can... - Map different user accounts to build a baseline of expected behavior for each individual user and entity.
- Identify anomalous user behavior based on activity time, count, and pattern.
- Get more meaningful security context by associating a user's different actions with each other.
- Spot abnormal entity behaviors in Windows devices, SQL servers, FTP servers, and network devices such as routers, firewalls, and switches.
- Expose threats emanating from insider attacks, account compromise, and data exfiltration.



