Accelerate incident response with Log360
Stay ahead of attackers by instantly detecting and responding to security incidents with the help of Log360, a unified SIEM solution.
Incident response refers to the steps undertaken by a security operations center to detect and respond to a cyberattack, contain the damage that might be caused, and prevent similar attacks from occurring again in the future. Attackers leverage the amount of time it takes a security team to discover malicious activity in their network: The more time taken by the security team to detect and respond to a breach, the more expensive it is for the organization to recover from the cyberattack.
An effective incident response plan can help an organization detect, investigate, and respond to security incidents quickly, thus avoiding data exfiltration and irreversible damage to the organization's reputation.
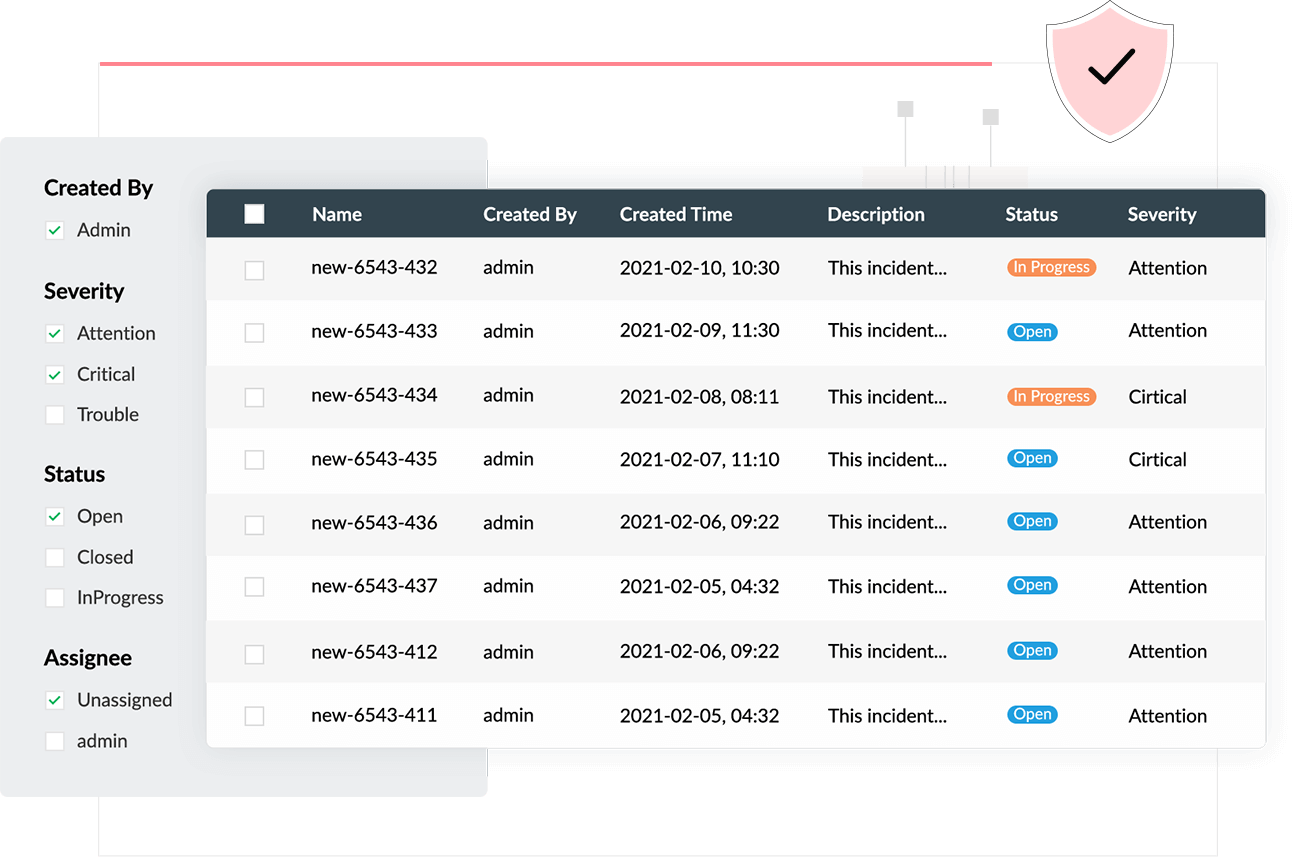
An intuitive security incident dashboard
Gain in-depth information about each security incident in the network from Log360's incident dashboard. With security incidents sorted by priority and source, Log360 helps you keep track of each security incident from detection to resolution.
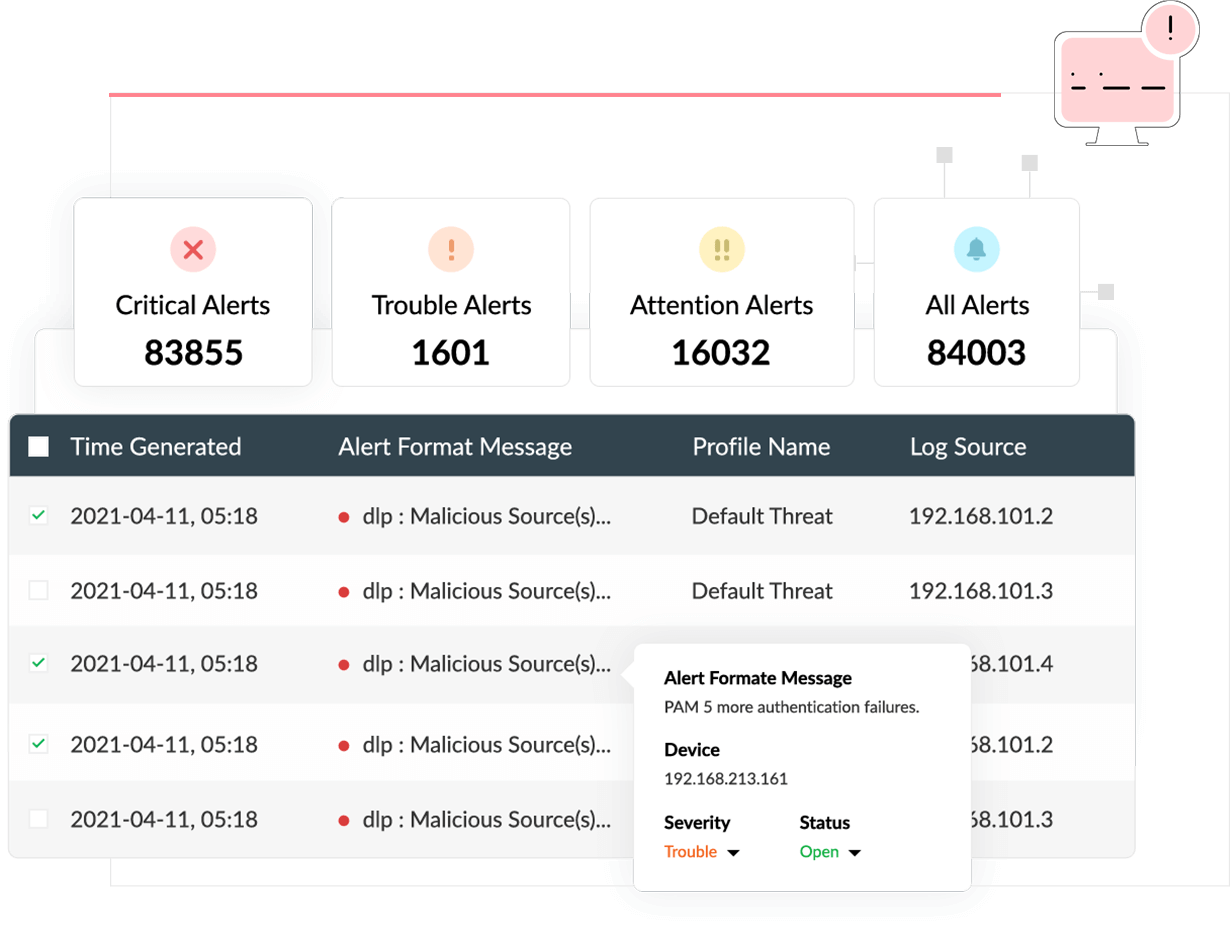
Real-time alerts and notifications
Get instant notifications via email or SMS when any security incident occurs in your organization's network. Log360 comes with more than 1,000 predefined alert criteria addressing a wide variety of security use cases. With the alerts categorized into three severity levels—Attention, Trouble, and Critical—you can prioritize high-risk incidents and resolve threats faster. Log360 also enables you to create and customize new alert profiles as per your requirements.
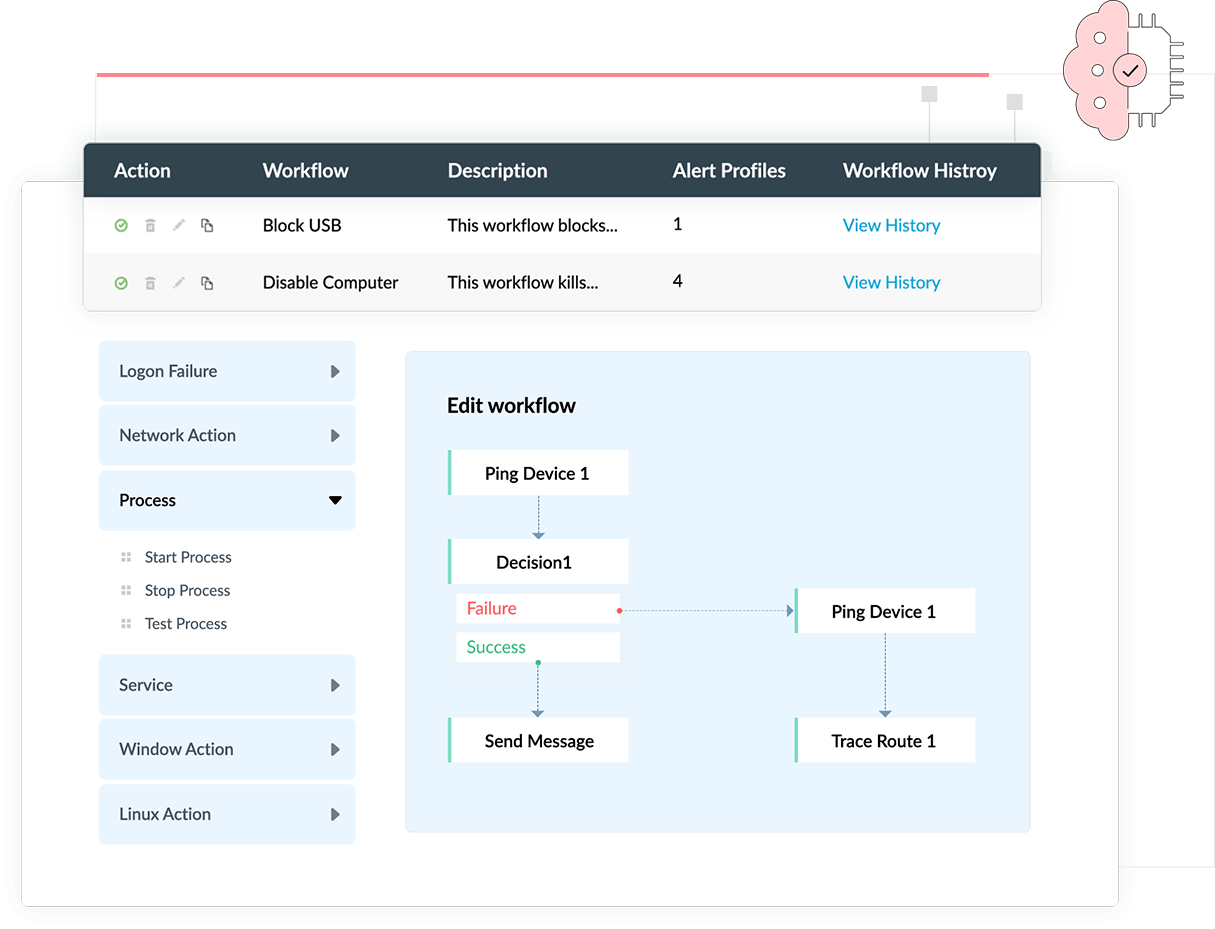
Automated incident response workflows
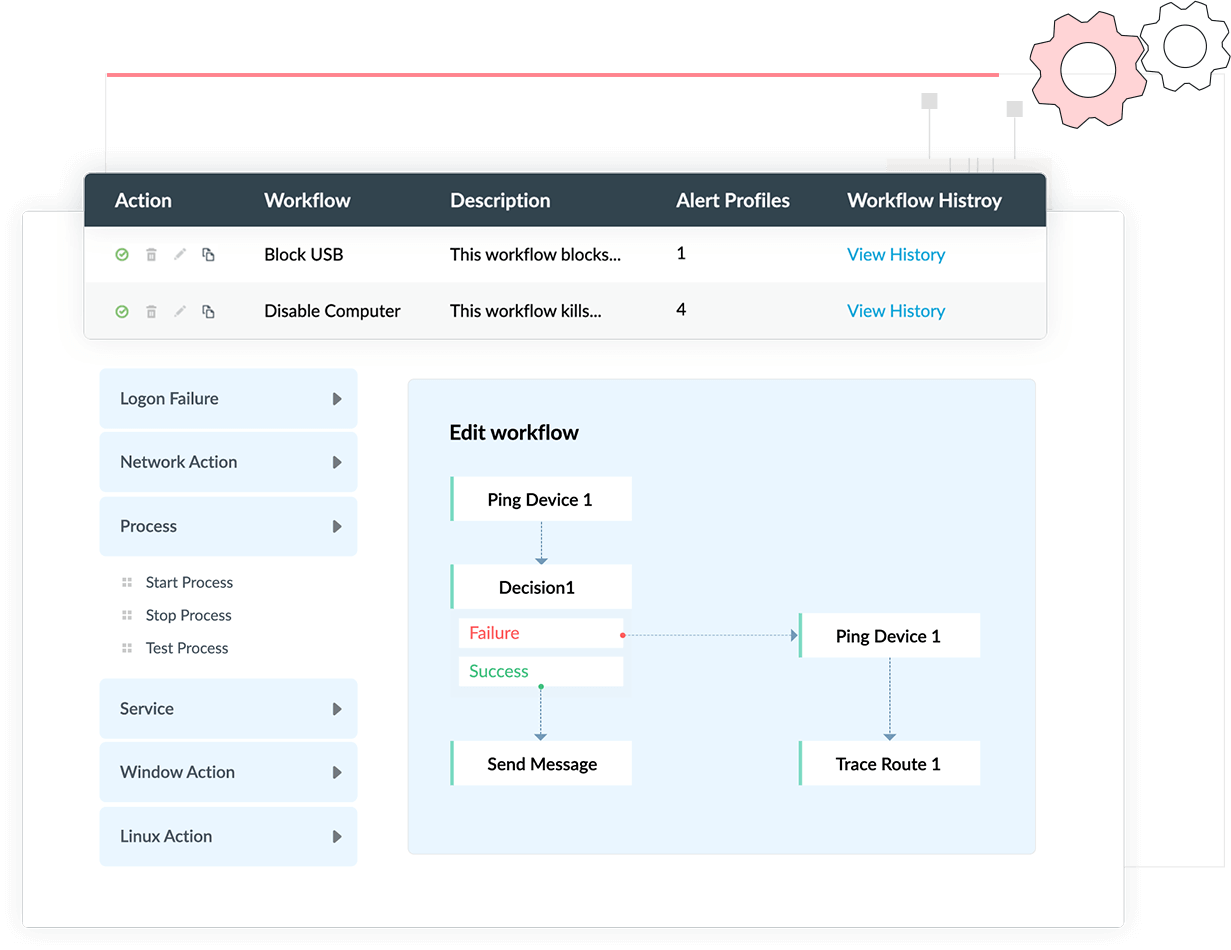
Log360 provides an option to design customized workflows using a simple drag-and-drop interface to mitigate the impact of any cyberattack. These incident workflows are automatically triggered when an alert is raised and act as an immediate response to a security incident before the intervention of the security administrator. You can automate responsive actions such as shutting down compromised devices, disabling USB ports, changing firewall rules, or deleting compromised user accounts.
Workflows can also be integrated with other applications and platforms, including
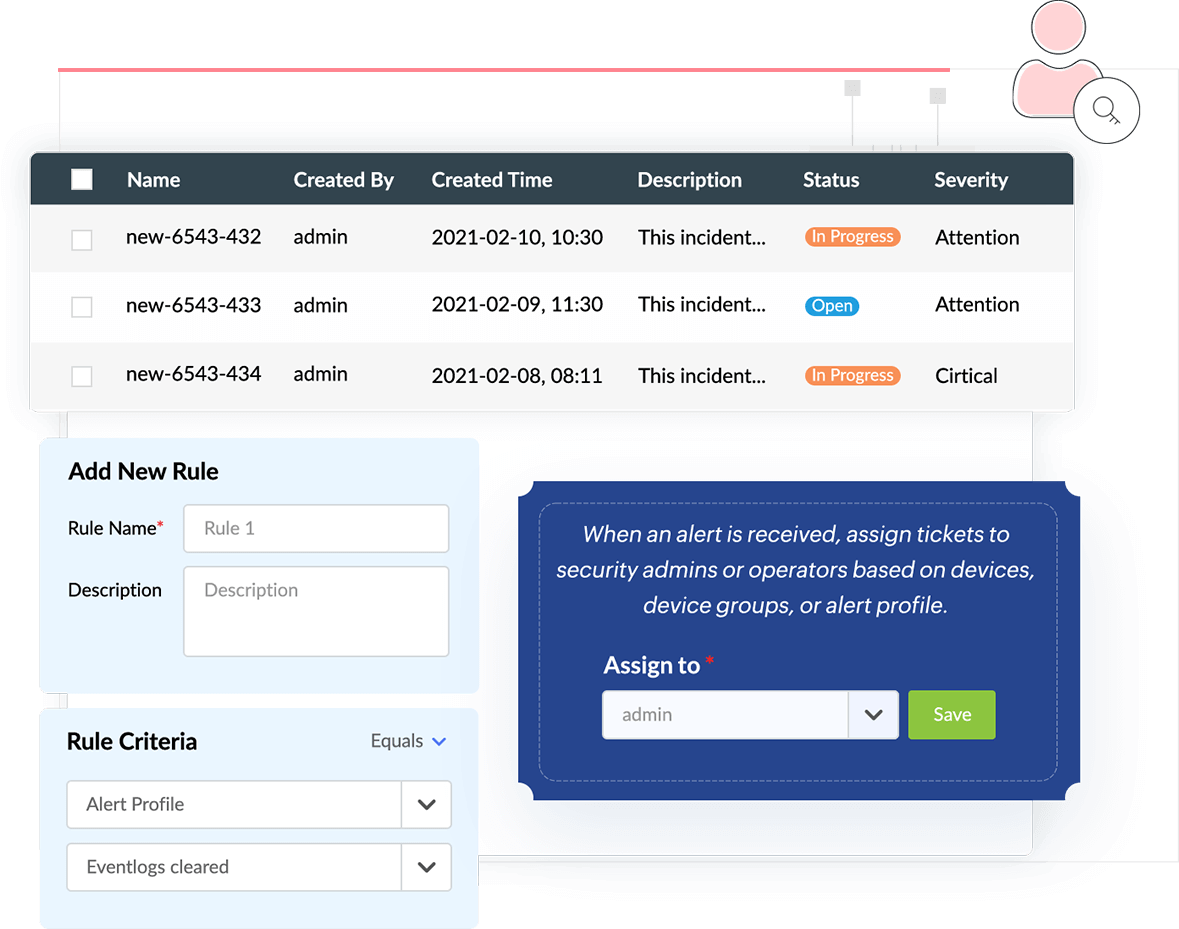
Automatic ticket assignment
Log360 generates tickets automatically when an alert is triggered. The tickets are assigned to the appropriate security administrator based on the device or device group that raised the alert. You can also track the status of the ticket on the incident dashboard.
Integration with external help desk tools workflows
Apart from being able to raise tickets within the Log360 console, you can also integrate Log360 with other external help desk software to create tickets automatically when alerts are triggered. The ticket can be further assigned to a suitable security administrator in your organization for resolution.
Log360 supports the following help desk software:
Why choose Log360 for incident response?
-
Security analytics
Gain deep insights into key network events using more than 1,000 predefined reports. Also comply with IT regulations such as PCI DSS, HIPAA, and the GDPR by using Log360's pre-existing, audit-ready report templates or by customizing your own.
-
Advanced threat intelligence
Integrating with open source and commercial threat feeds enables Log360's threat intelligence platform to accelerate incident detection by raising real-time alerts when a malicious IP address interacts with your network.
-
Real-time event correlation
Identify various attack patterns in your network with the help of Log360's powerful log correlation engine. With over 30 built-in correlation rules and a custom rule builder, Log360 helps you detect network threats quickly.
-
User and entity behavior analytics
With the help of machine learning techniques, Log360's UEBA module helps you detect anomalous behavior in your organization's network.



