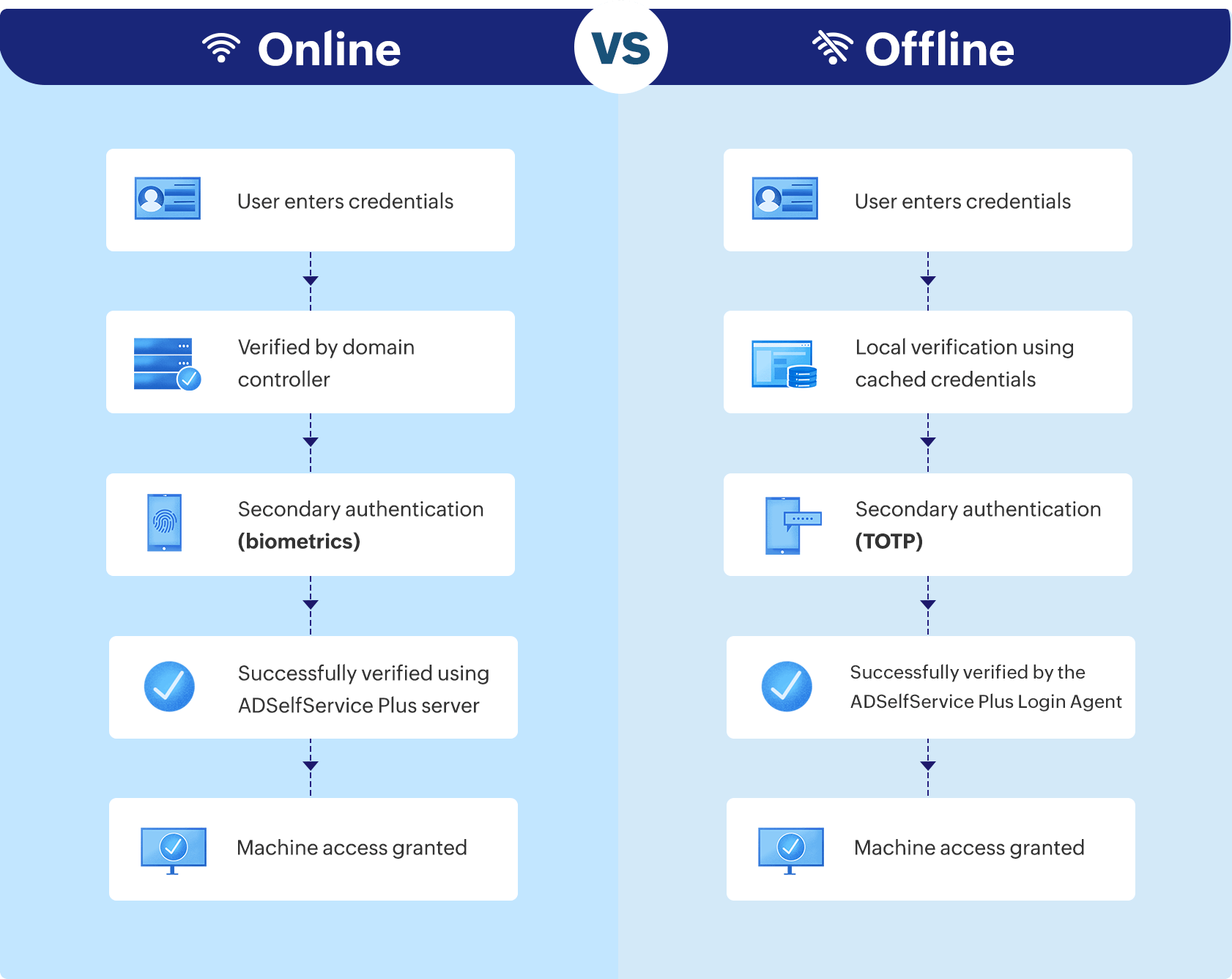
Normally, for MFA to function, users' devices must be connected to the internet or to the same network as the MFA server to communicate authentication information. But, due to unforeseen conditions, connection to the MFA server can sometimes be severed, taking the user offline. In such cases, bypassing MFA or blocking access are both unwise options.
Offline MFA bridges the gap, allowing you to enforce MFA for your users even when they have no access to the MFA server. This way, your users' offline status does not have to limit your organization's cybersecurity.
ManageEngine ADSelfService Plus supports offline MFA for Windows and macOS machine logins. Admins can configure one or more MFA factors for users to authenticate with. Users need to enroll themselves in the respective authenticators when they are online so that they can perform MFA when they are offline.
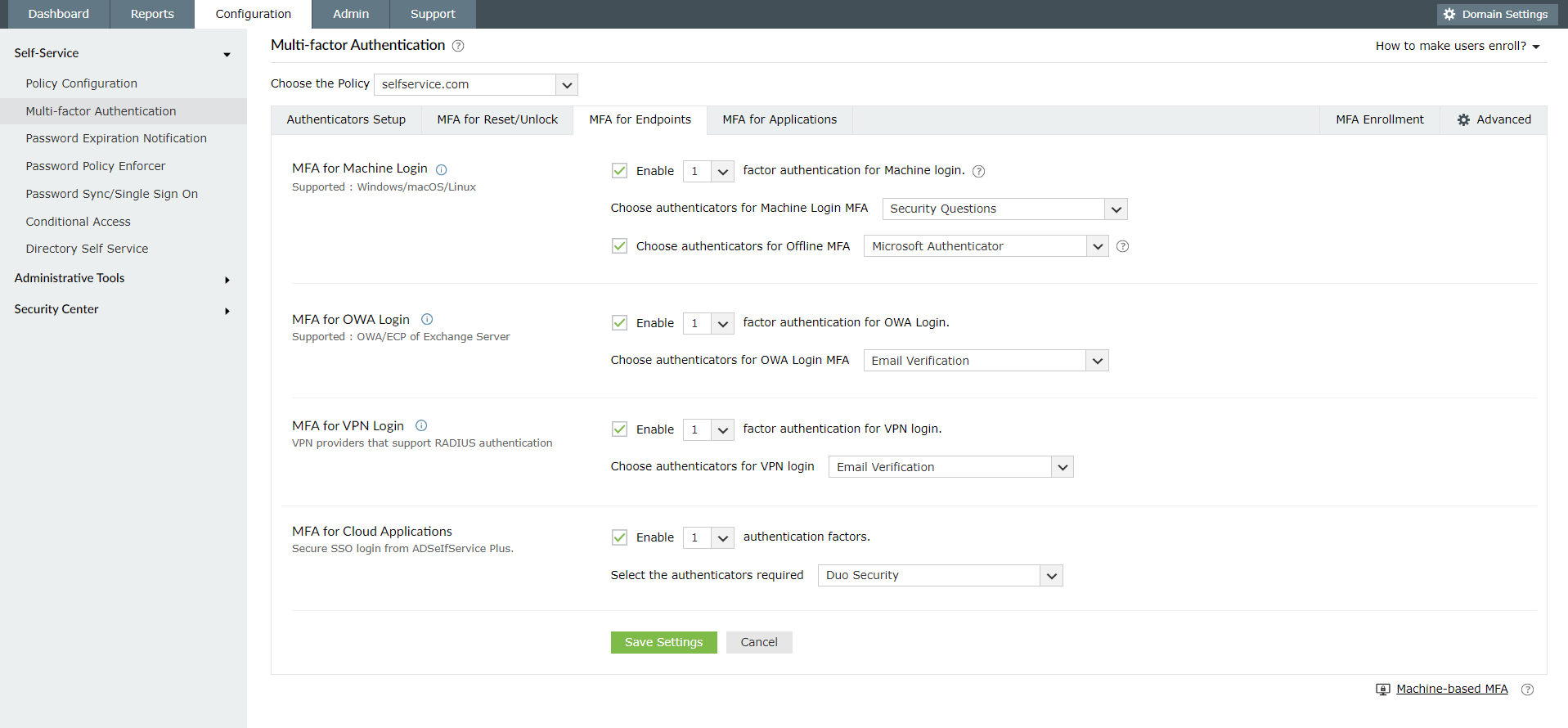
Decide whether you want to enable offline MFA in your organization and choose the authentication factors you want to use.
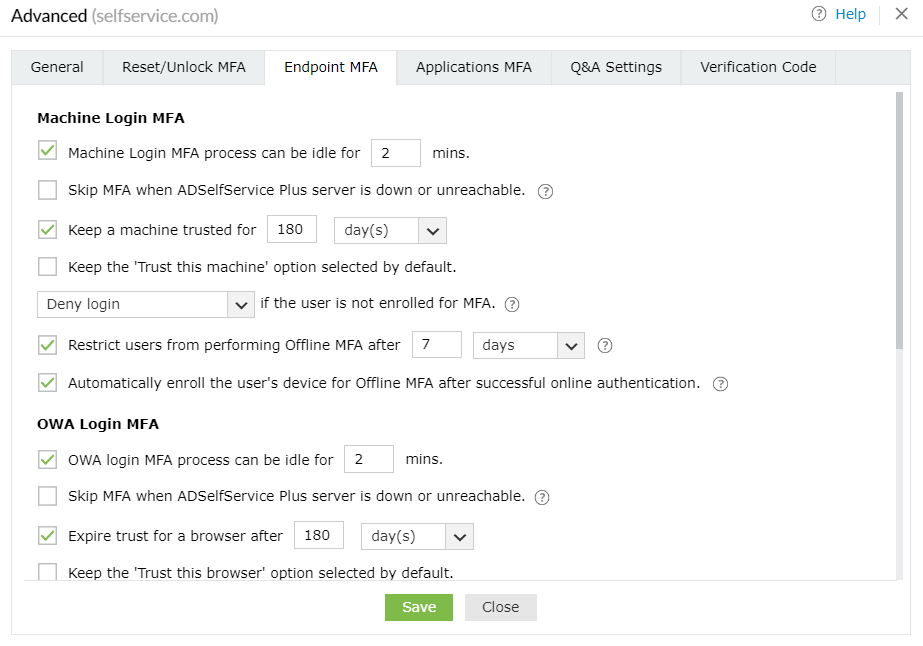
Choose between letting your users enroll in offline MFA themselves or automatically enrolling them in offline MFA on a particular device.
Set the number of times a user can perform offline MFA based on the number of attempts or the number of days, after which they have to perform online MFA at least once.
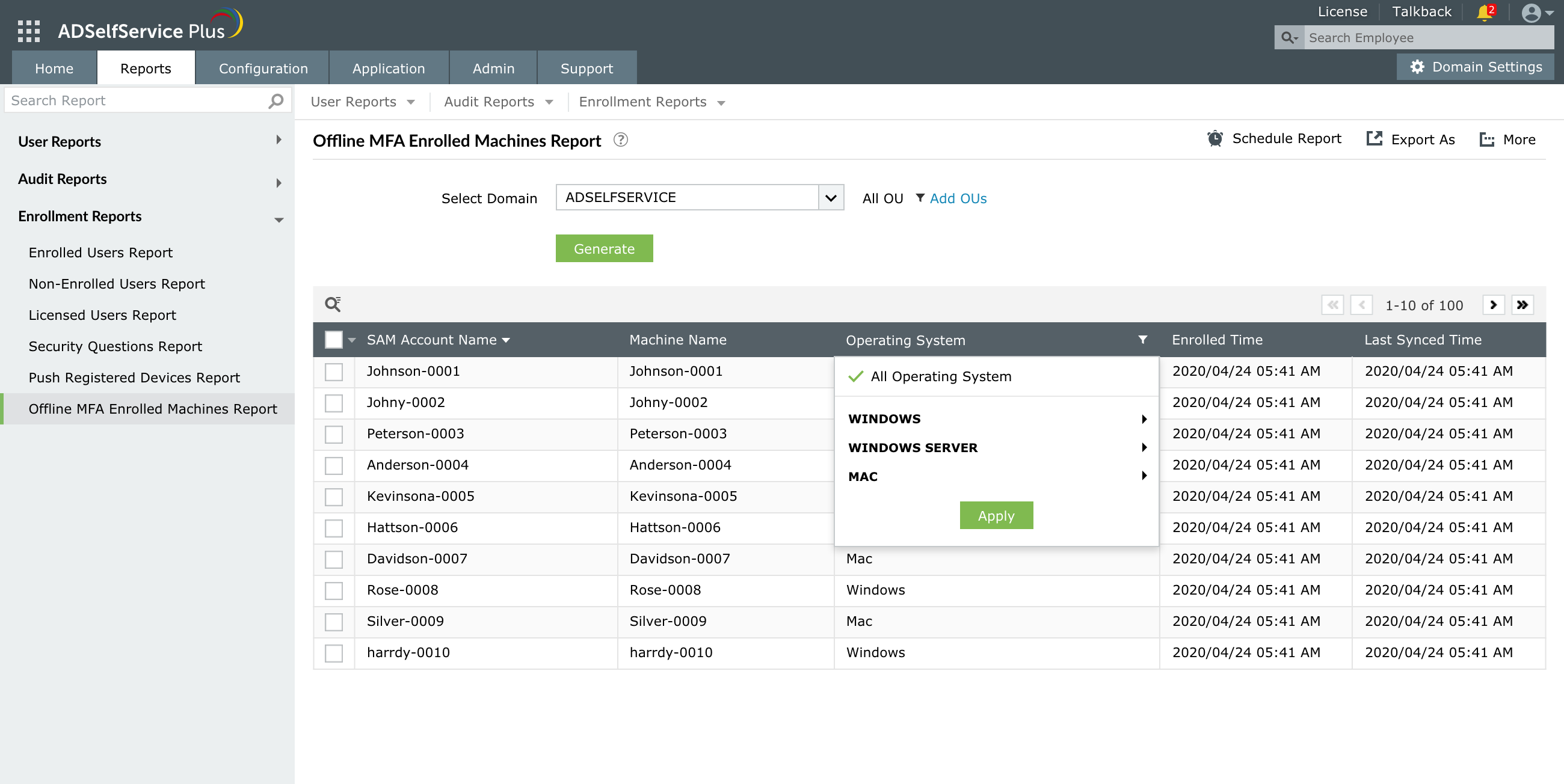
Generate a consolidated report of users who have enrolled in offline MFA, along with timestamps, and disenroll users if needed.
Offline MFA will work in both of the following scenarios:

Note: Users who choose to skip MFA enrollment will not be able to prove their identities through MFA during login. Based on the admin-enabled configurations, either MFA will be bypassed for them, or they will not be able to access their machines.
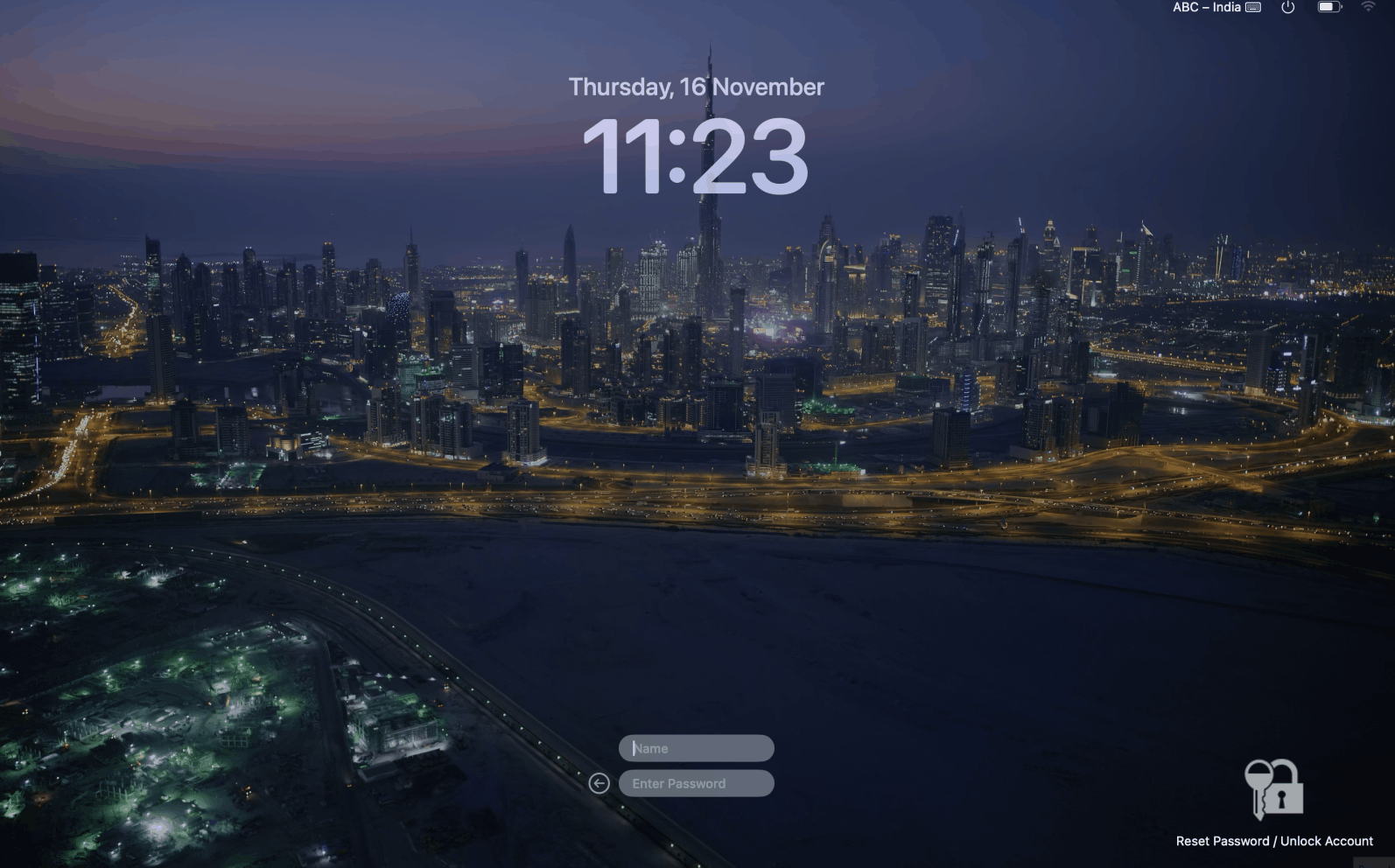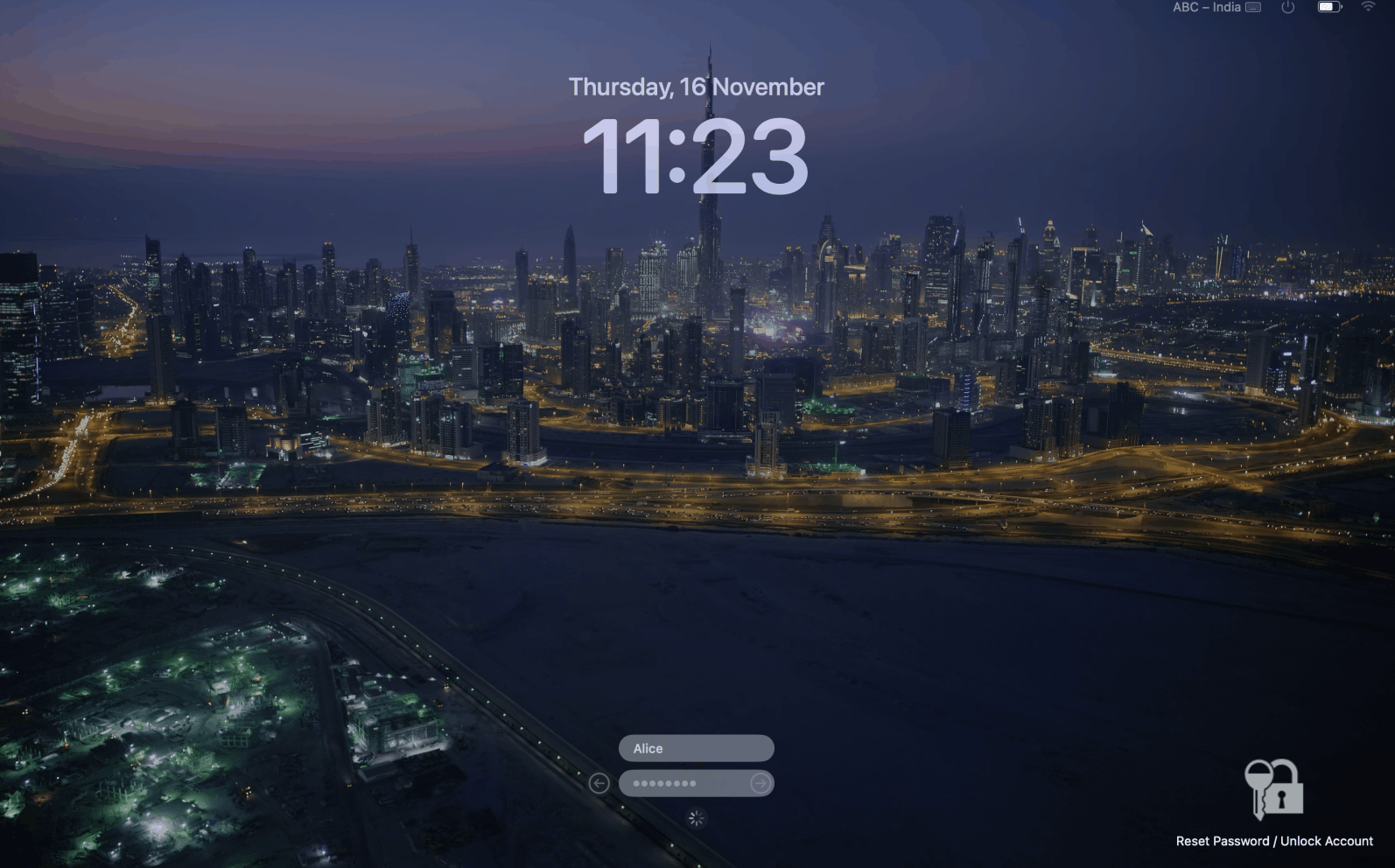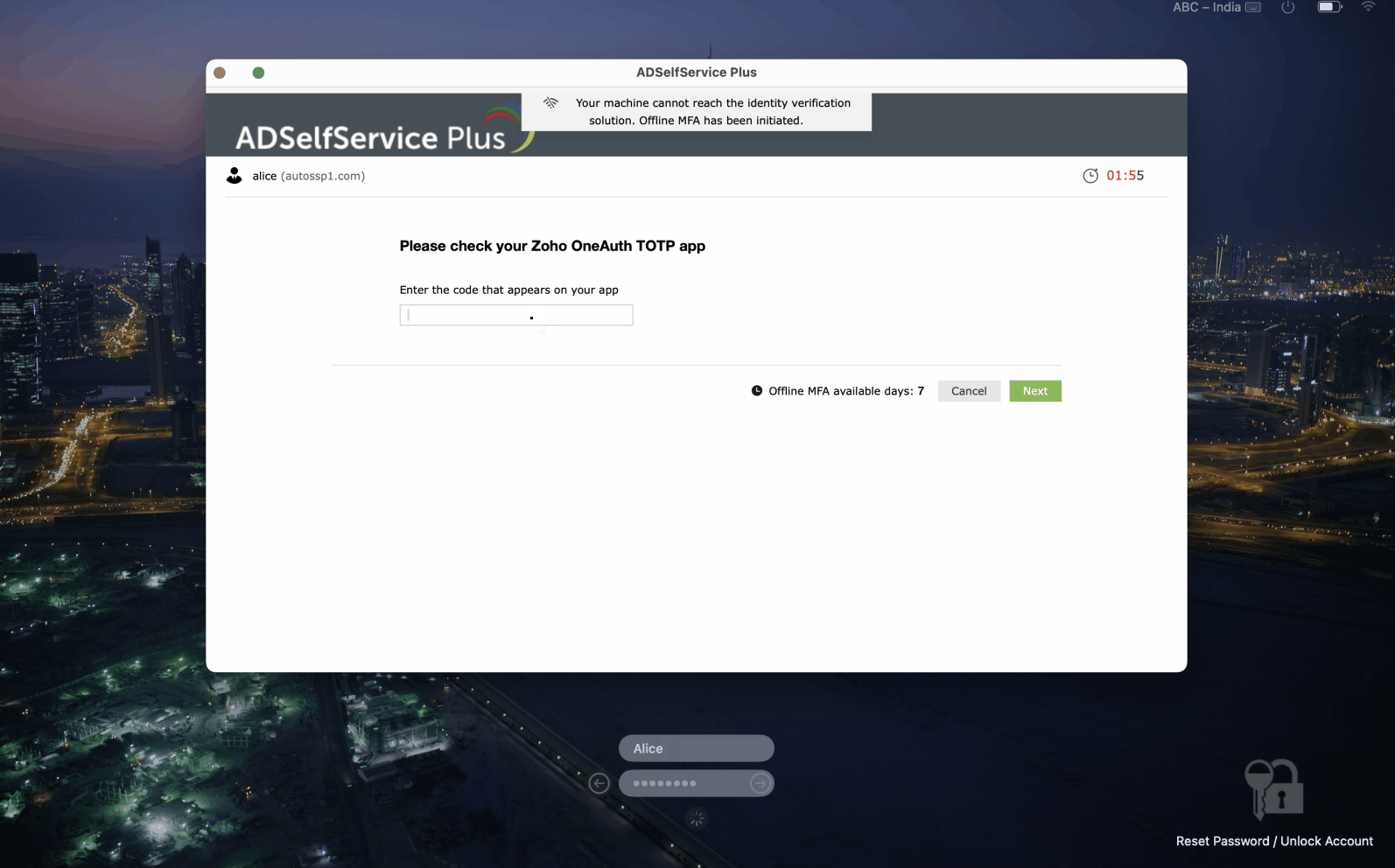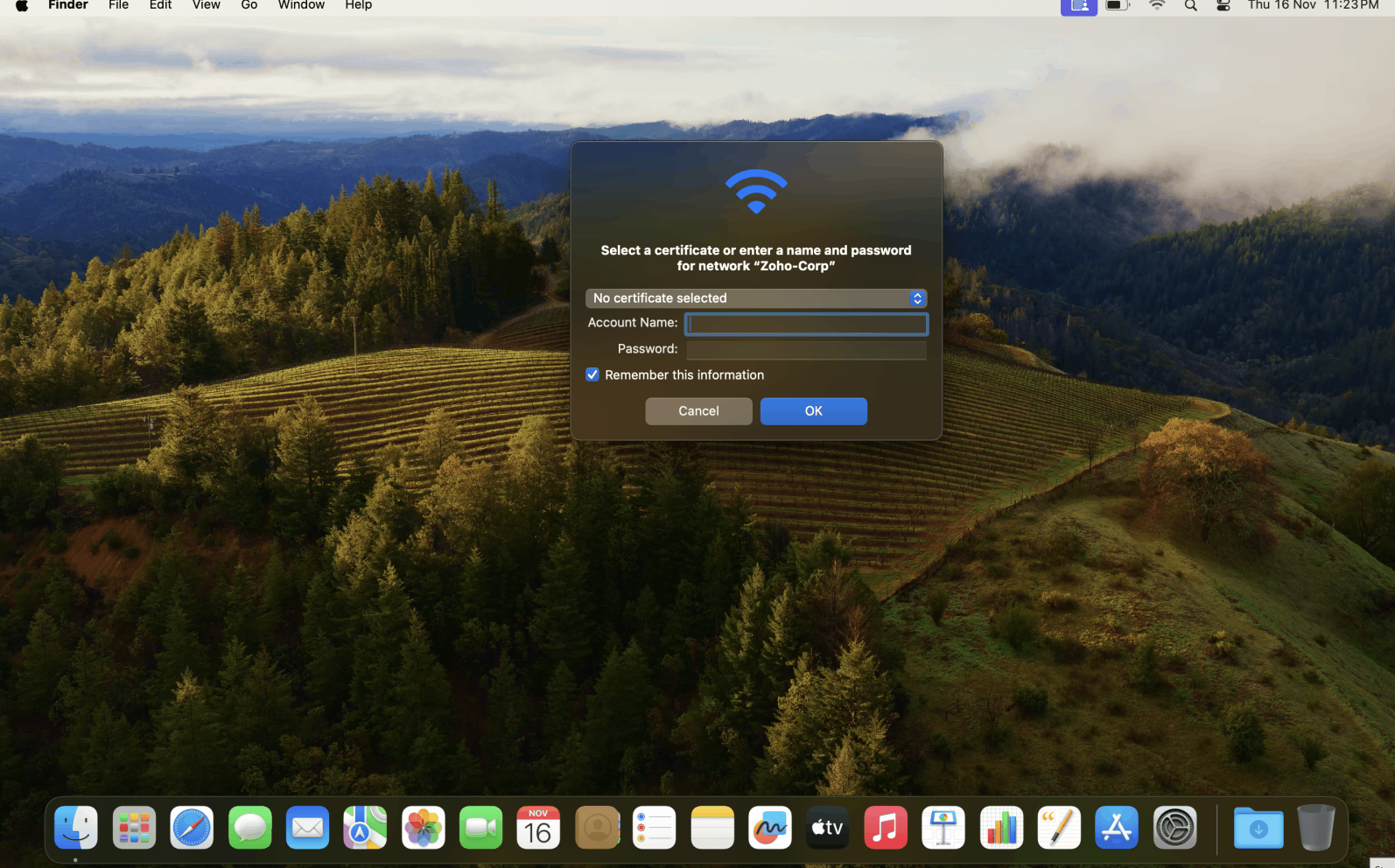
Note: Users who choose to skip MFA enrollment will not be able to prove their identities through MFA during login. Based on the admin-enabled configurations, either MFA will be bypassed for them, or they will not be able to access their machines.
ADSelfService Plus supports the following authenticators for offline MFA:
Rest assured that your users' machines are secured with MFA whether they are working remotely or have connectivity issues.
Generate readable, consolidated reports of users who have enrolled in offline MFA, along with the timestamps, and disenroll users if necessary.
Allow users to enroll in offline MFA on multiple devices.
Enable context-based MFA with 19 different authentication factors for endpoint and application logins.
Learn moreAllow users to access all enterprise applications with a single, secure authentication flow.
Learn moreEnhance remote work with cached credential updates, secure logins, and mobile password management.
Learn moreEstablish an efficient and secure IT environment through integration with SIEM, ITSM, and IAM tools.
Learn moreDelegate profile updates and group subscriptions to end users and monitor these self-service actions with approval workflows.
Learn moreCreate a Zero Trust environment with advanced identity verification techniques and render your networks impenetrable to threats.
Learn more