Identity360 provides one-click access to enterprise resources with secure single sign-on
Approximately 68% of employees switch between 10 apps every hour.*
To make life easier, 59% of employees use the same password on multiple accounts. †
The hassle of logging in has caused approximately 26% of IT employees to give up doing something. ‡
Identity360 equips and empowers your organization with modern SSO capabilities.
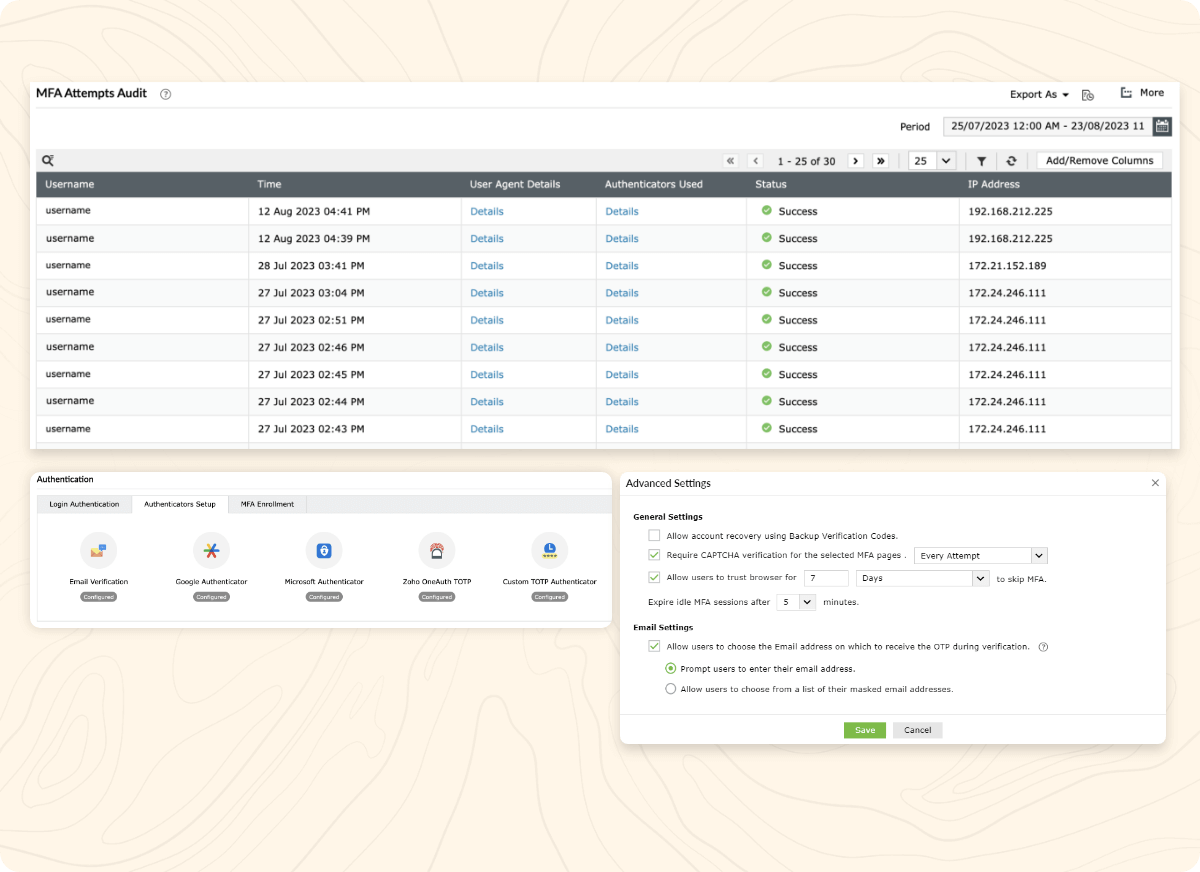
Identity360 secures SSO with strong MFA factors, like email verification, Google Authenticator, and custom TOTP authenticators. Up to three authenticators can be configured for identity verification and they can be customized using granular controls. The solution also provides elaborate MFA reports to help you track all MFA attempts made by users, along with timestamps, and the outcome of each attempt.
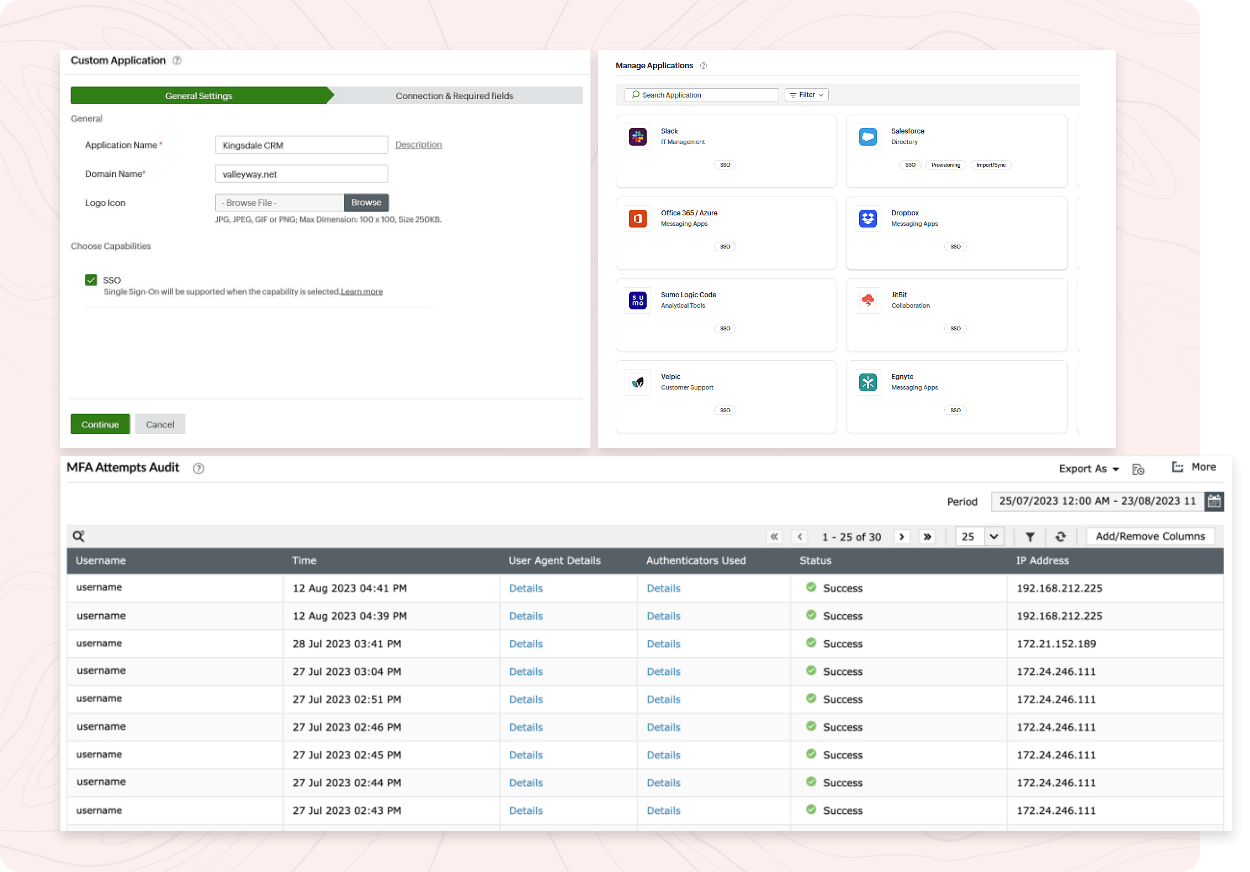
SSO can be enabled easily for a myriad of pre-integrated applications using Identity360. Apart from these pre-integrated applications, you can also easily integrate your own custom applications for end-user SSO. With a user-friendly UI, Identity360 provides an enriched, interactive experience for both admins and end users in their SSO journey.
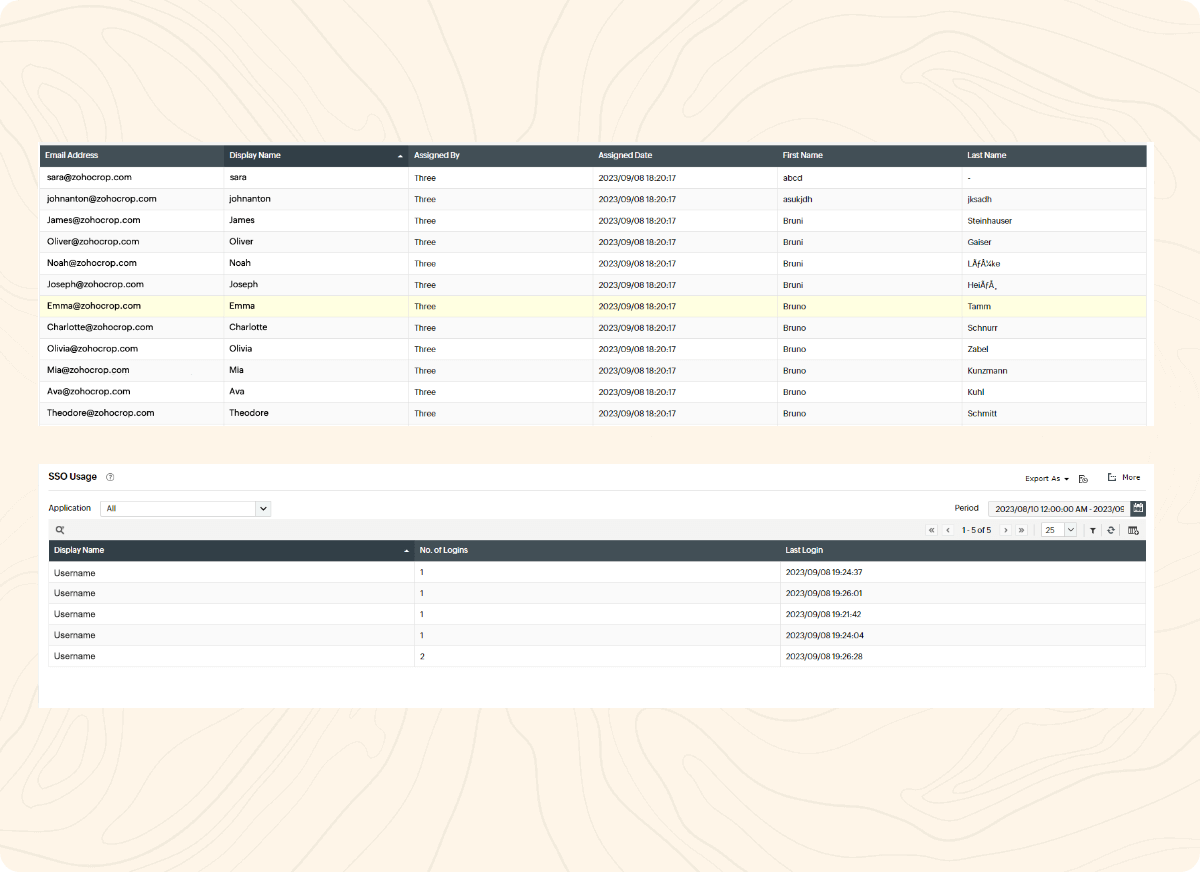
Identity360 makes the tracking of end user SSO activity easy for admins by generating elaborate SSO reports. These reports capture data like the applications assigned to each user, the number of logons, and the last logon time of a user in each application. These reports can be customized by adding or removing columns, and by filtering necessary data. Moreover, the reports can be exported in various file formats—like PDF, CSV, XLS, and HTML—for further analysis.
Here's how SSO works in Identity360 when a user tries to access resources:
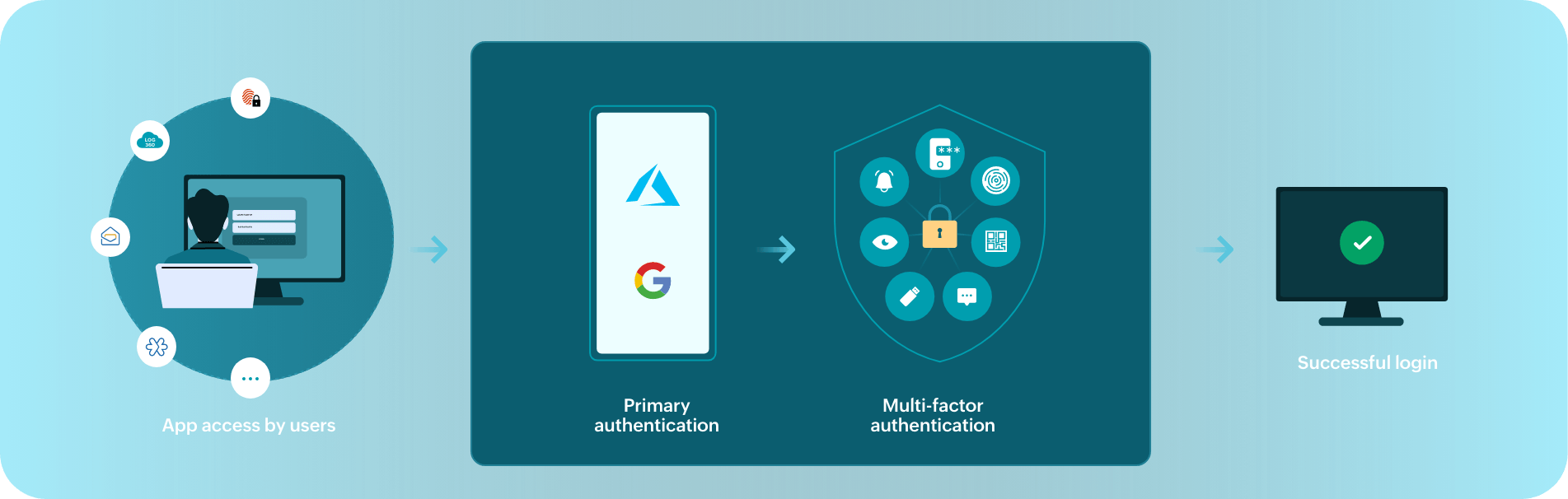
When a user tries to access an application directly or through Identity Manager Plus, they have to verify their identity via two stages: primary authentication and secondary authentication.
In primary authentication, the user's credentials are verified against their primary directory through the OIDC protocol.
Secondary authentication is performed after the successful completion of the primary authentication, where they have to verify with admin-configured MFA methods.
Upon successful completion of MFA, the user gains access to all enterprise applications assigned to them through SSO for a specific duration, after which they have to re-authenticate.
Identity360 provides users with one-click access to enterprise apps, thereby eliminating password fatigue and time-consuming login processes.
With modern MFA authenticators and granular MFA customization capabilities, each SSO attempt is well protected against potential security threats.
Identity360 provides secure SSO to a range of enterprise applications, both pre-integrated and custom, in a just a few easy configuration steps.
Without SSO, your users will have multiple credentials to manage every day. Repeated logons to various platforms causes fatigue in users and decreases their productivity. Moreover, users handling multiple credentials themselves almost always means increased password management workload for admins. Identity360 gives your users secure, one-click access to enterprise applications using SSO. A vast range of pre-integrated and custom applications are supported and each SSO attempt is secured with customizable MFA techniques.
Single sign-on or SSO is the process of giving users one-click access to multiple enterprise resources after an initial identity verification step. SSO allows users to access the resources assigned to them for a specific duration, afterward they have to re-authenticate.
SSO, when backed by strong authentication factors, provides a reliable way to protect resources and improve the user experience at the same time. To fortify SSO in your organization, you can implement granular SSO controls. These controls include limiting the duration of each SSO session, allowing users to enable browser trust only for known and trusted devices, and providing them with SSO access to the right resources.
You can implement SSO with Identity360, which secures all application logins with modern MFA methods. It provides fine-grained MFA and SSO controls that can be customized to suit your organizational needs. Using consolidated SSO reports, you can track details like the applications assigned to each user, the number of logons, and the last logon time of a user against each application.
To gain a better understanding of Identity360's SSO capability, please schedule a personalized web demo with our solution experts.
Source: *LastPass, †Yubico, ‡1Password