Sensitive data discovery & classification
What is sensitive data discovery?
Sensitive data discovery is the process of finding and classifying sensitive information within an organization's endpoints. Information sensitivity is a set of methods for controlling access to sensitive data that could harm a company if it is revealed to others. By identifying and monitoring this type of data, such as personally identifiable information (PII), financial records, and health records, organizations can ensure that their sensitive data is protected.
How is endpoint data discovery implemented?
Endpoint Central has a complete endpoint sensitive data discovery mechanism with the following capabilities:
- Scan all managed endpoints for structured and unstructured data.
- Perform a forensic evaluation of the data to gather qualitative and quantitative insights, which admins can use to gain a better understanding of their data.
- Identify the users and endpoints associated with particular types of data, which is important for mitigating data loss and insider threats.
- Once the location of data is known, it is scanned for further analysis. Data discovery is the first step in data classification.
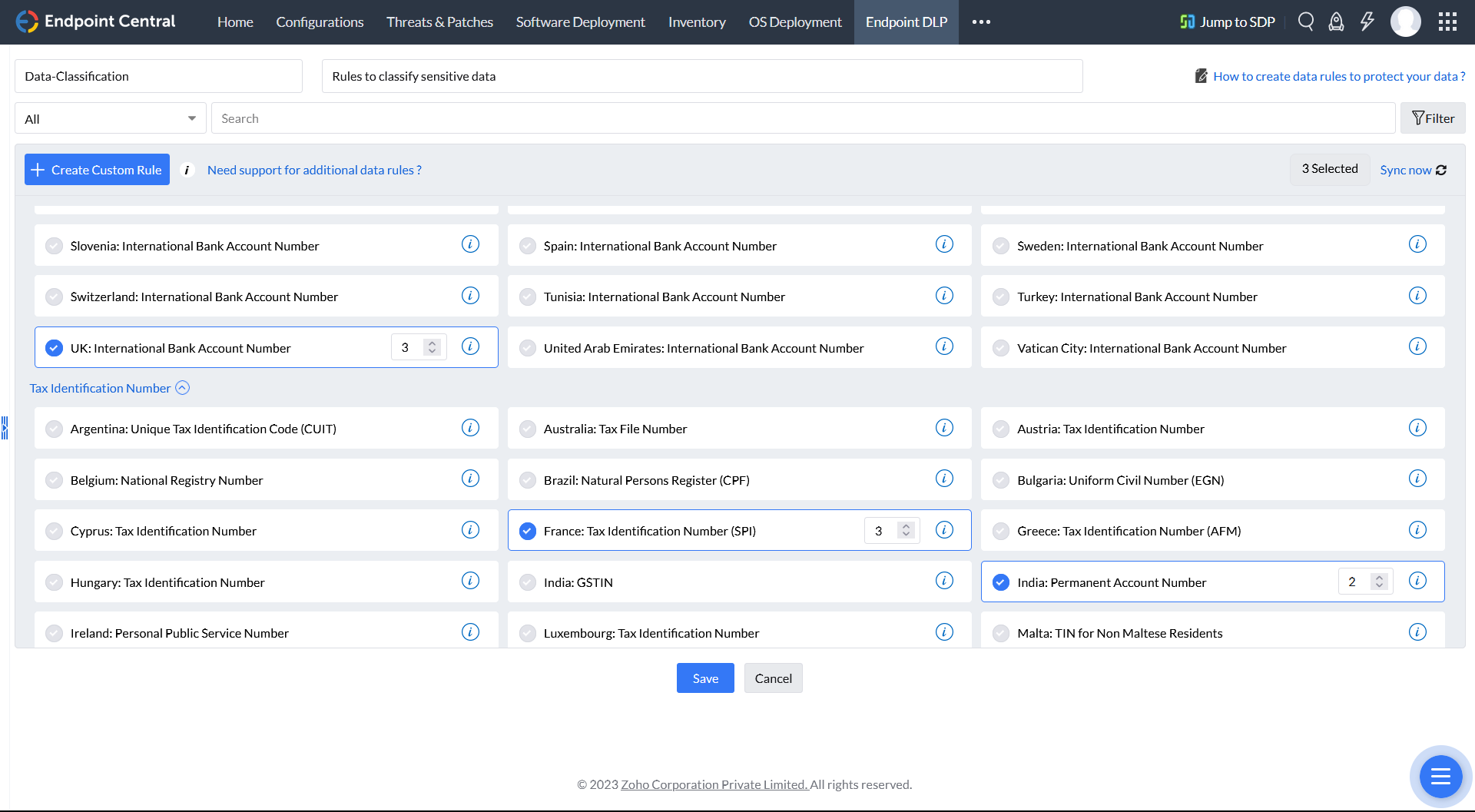
Why is data classification important?
Businesses collect a vast amount of data at any given time, including sensitive information that may be transferred inadvertently during informal exchanges. Data classification software helps administrators identify and protect sensitive data by distinguishing between harmless information and confidential information that requires safeguarding.
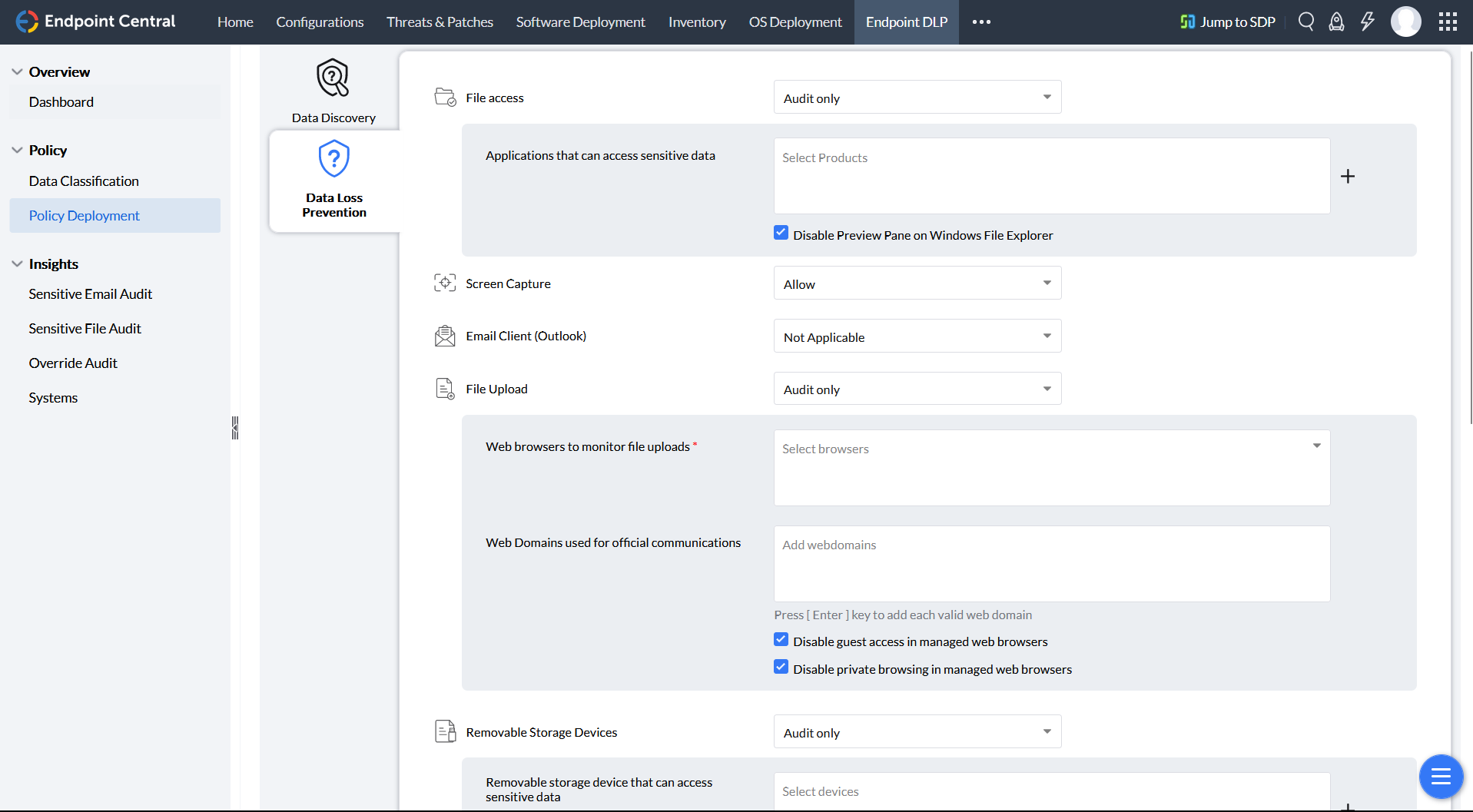
Data leak prevention
Data loss prevention (DLP) is a critical security strategy for protecting sensitive enterprise data from theft, loss, or unauthorized access. A comprehensive DLP solution includes tools for data discovery and classification, data transfer and access control, policy and incident management, and detailed auditing and alerting.
Why is DLP essential?
DLP prevents the impact of data loss and theft, which can have devastating consequences for businesses. For example, a data breach can lead to:
- Financial losses from fines, lawsuits, and customer churn
- Damage to reputation and brand trust
- Loss of competitive advantage
- Regulatory compliance violations
How does data loss happen?
Data loss can happen in a variety of ways, including:
- Human error: Accidental deletion, overwriting of files, or sending data to the wrong person.
- Cyberattacks: Malware, ransomware, and phishing attacks can all lead to data loss or theft.
- Physical loss or theft: Laptops, mobile devices, and other storage devices can be lost or stolen.
DLP helps to mitigate these risks by:
- Identifying and classifying sensitive data, so that it can be protected more effectively
- Monitoring and controlling data transfer and access, to prevent unauthorized users from accessing sensitive data
- Enforcing policies to reduce the risk of human error
- Detecting and responding to data breaches and other security incidents
- Auditing and alerting on data activity, so that organizations can quickly identify and address potential problems
Do you need a DLP solution?
Any organization that collects, stores, or processes sensitive data should consider implementing a DLP solution. DLP is especially important for businesses in regulated industries, such as healthcare, finance, and government.
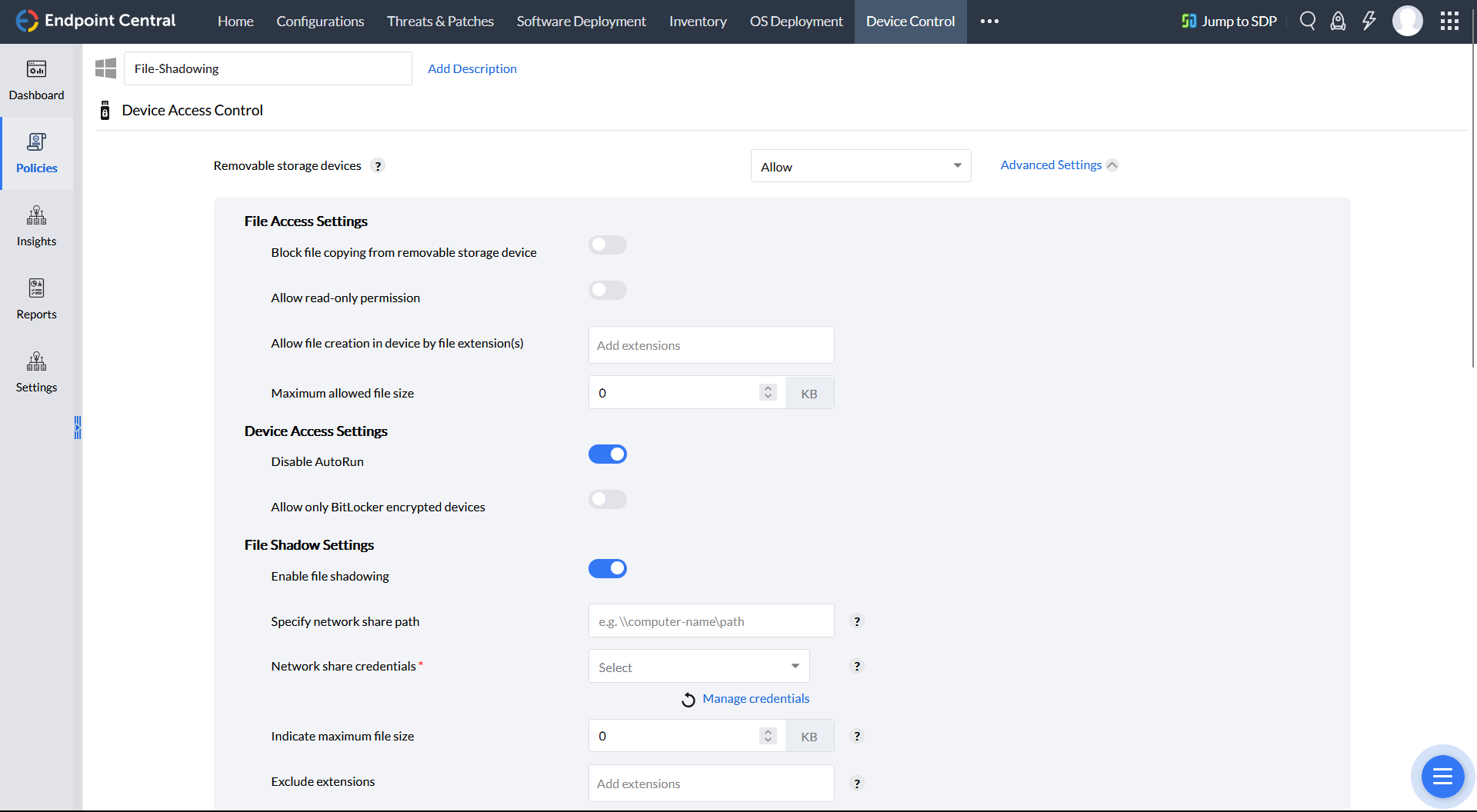
Trace and mirror files
Data mirroring is a security measure that creates copies of sensitive data on USB devices when they are connected to a network. This data can then be stored in a secure location, such as a password-protected network share.
Data mirroring software can be used to configure policies to ensure that data mirroring happens whenever any file action is carried out on a USB, or just when specific file actions are performed. Details regarding the file operation, such as file name, users, devices, endpoints involved, and the time of action, can also be recorded.
Benefits of data mirroring:
- Protects corporate data from theft or loss: If a USB device is lost or stolen, the data can still be accessed from the secure network share.
- Helps to comply with regulations: Many regulations require businesses to have safeguards in place to protect customer data. Data mirroring can help businesses to meet these requirements.
- Provides visibility into data movement: Data mirroring can provide organizations with valuable insights into how data is being moved around the network. This information can be used to identify and address potential security risks.
Considerations:
- Bandwidth and disk space requirements: Data mirroring requires considerable bandwidth and disk space. Businesses need to carefully consider their needs before implementing a data mirroring solution.
- Policy configuration: It is important to carefully configure data mirroring policies to ensure that the right data is being mirrored and that the data is stored in a secure location.
Overall, data mirroring is a versatile and powerful tool that can be used to improve the security, compliance, and performance of IT systems.
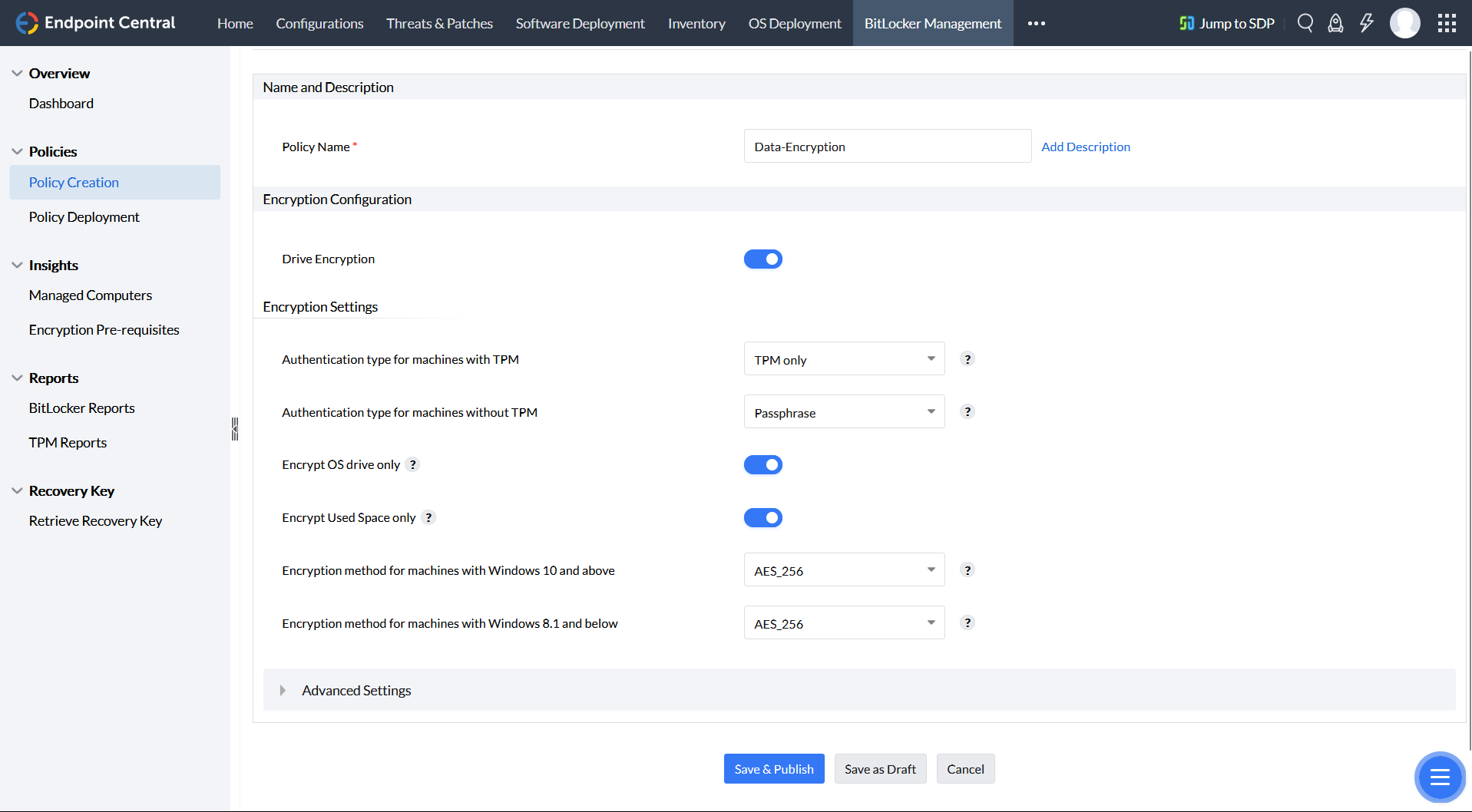
Data Encryption
Endpoint Central is a unified endpoint management and security (UEMS) solution that enables IT administrators to seamlessly manage BitLocker encryption on Windows devices across their networks. This helps organizations to ensure that their data is encrypted and protected from unauthorized access, even if a device is lost or stolen.
Benefits of using Endpoint Central to manage BitLocker encryption:
- Centralized management: Endpoint Central provides a single console for managing BitLocker encryption on all Windows devices across the network. This makes it easy for IT administrators to deploy and enforce BitLocker encryption policies, and to monitor the encryption status of all devices.
- Automated encryption: Endpoint Central can automatically encrypt Windows devices based on predefined policies. This eliminates the need for IT administrators to encrypt each device manually, and helps to ensure that all devices are encrypted consistently.
- Comprehensive reporting: Endpoint Central provides comprehensive reports on the BitLocker encryption status of all devices. This helps IT administrators to identify and address any encryption issues quickly and easily.
How Endpoint Central can help organizations manage BitLocker encryption seamlessly:
- Deploy and enforce BitLocker encryption policies: Endpoint Central can be used to deploy and enforce BitLocker encryption policies on all Windows devices across the network. This includes configuring BitLocker encryption settings, such as password complexity requirements and encryption recovery key management.
- Monitor the encryption status of all devices: Endpoint Central provides a real-time view of the BitLocker encryption status of all devices across the network. This helps IT administrators to identify and address any encryption issues quickly and easily.
- Remotely manage BitLocker encryption: Endpoint Central allows IT administrators to manage BitLocker encryption on Windows devices remotely. This includes tasks such as encrypting and decrypting devices, and resetting the BitLocker recovery key.