Given the evolving IT threat landscape today, multi-factor authentication (MFA) has become a familiar security norm. While MFA is a well-known approach, it does not mean all organizations know how to apply it effectively. It's not enough to simply have an MFA solution in place; it's essential to develop a detailed strategy to make the best use of an MFA setup in order to render your network impenetrable. Another challenge is to implement an MFA solution that fortifies access to your IT resources but does not interfere with user productivity.
ADSelfService Plus offers 19 different authentication factors ranging from biometrics to TOTPs.
Learn moreConfigure MFA for VPN, OWA, and machine logins in just a few clicks from our user-friendly console. Set up different MFA flows for different groups or departments in your organization.
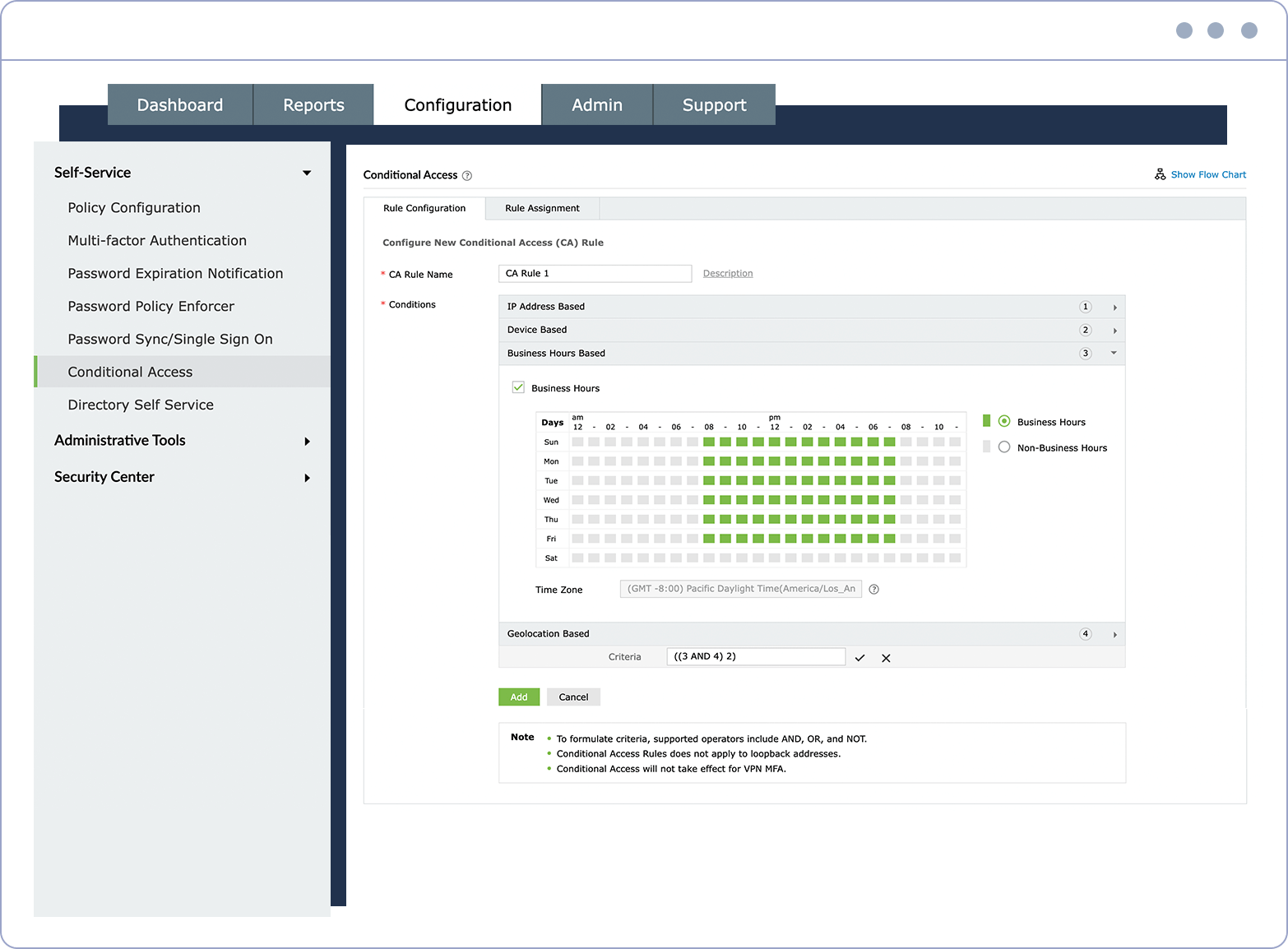
Learn moreFine-tune the access rules for IT resources such as applications and endpoints based on a user's location, IP address, time of access, and device used.
Learn moreEnable passwordless login for cloud and on-premises applications through SSO.
Learn moreAdaptive MFA, otherwise known as risk-based MFA, provides users with authentication factors that adapt each time a user logs in depending on the calculated risk level of the user based on contextual information. Some examples of contextual information include:
The authentication factors presented to the user are based on the risk level that is calculated using the above contextual factors. For instance, consider a user trying to log in to their work machine at an untimely hour while on a vacation. Since the user's geolocation and time of access are different, they are automatically prompted with additional authentication factors to prove their identity.
Sometimes, when the user's login conditions are checked and no risk is detected, the MFA process can be bypassed for the user. And sometimes, if the user's activity seems suspicious, they can also be denied access to the requested resource.
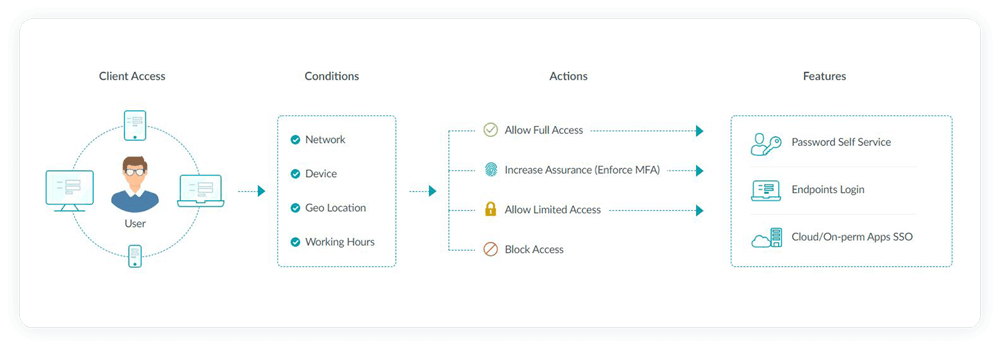
Customizable rules Create your own rules based on which adaptive authentication takes place.
Configurable conditions Choose from a wide range of conditions, such as IPs, business hours, and geolocation.
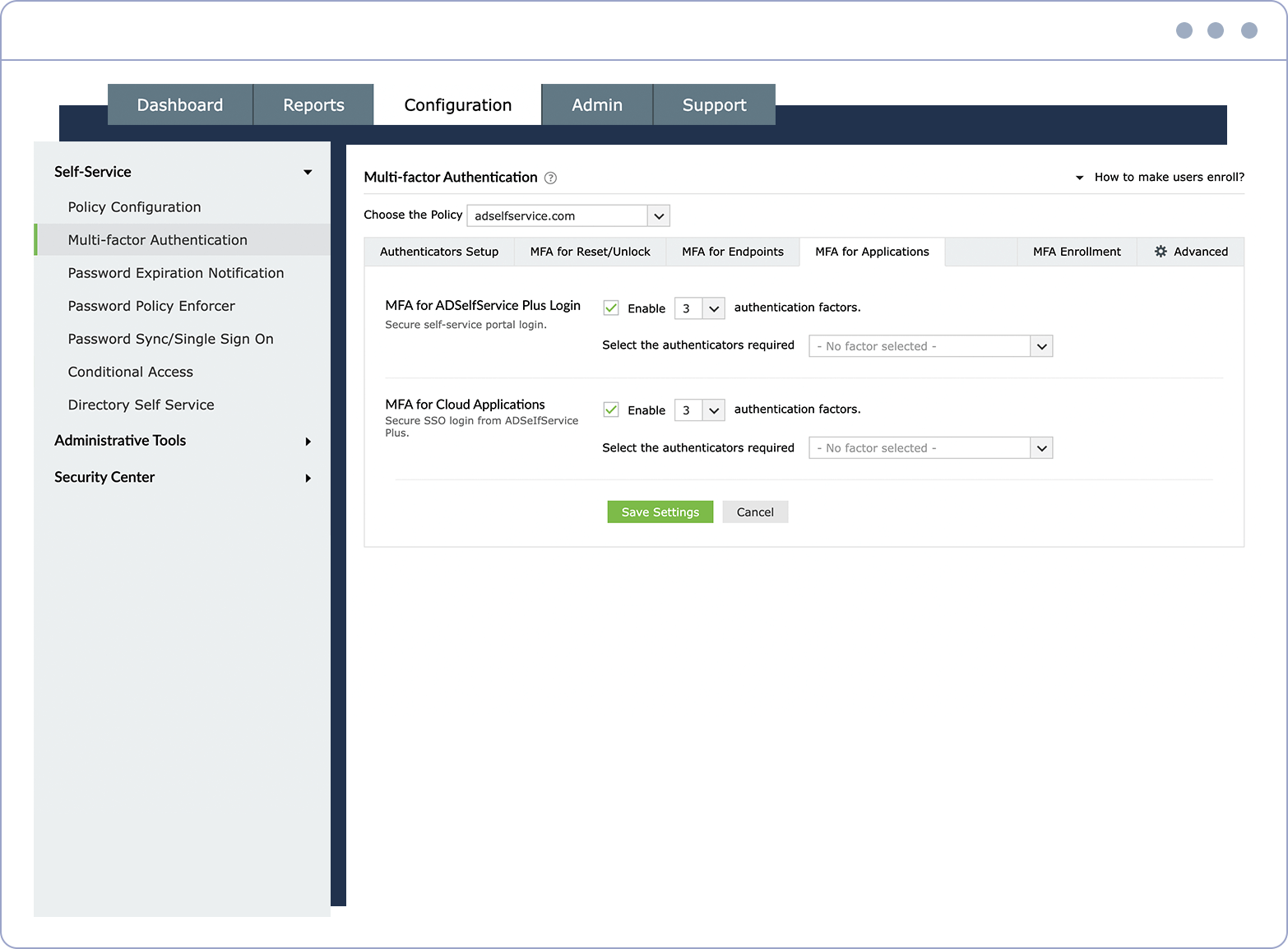
Customizable MFA Pick the number and type of MFA methods that your users must authenticate with to gain access to resources.
Secure self-service actions Configure MFA for user self-service activities like password resets and account unlocks.
Secure endpoints Configure MFA for endpoints, like machine, VPN, RDP, and OWA logons.
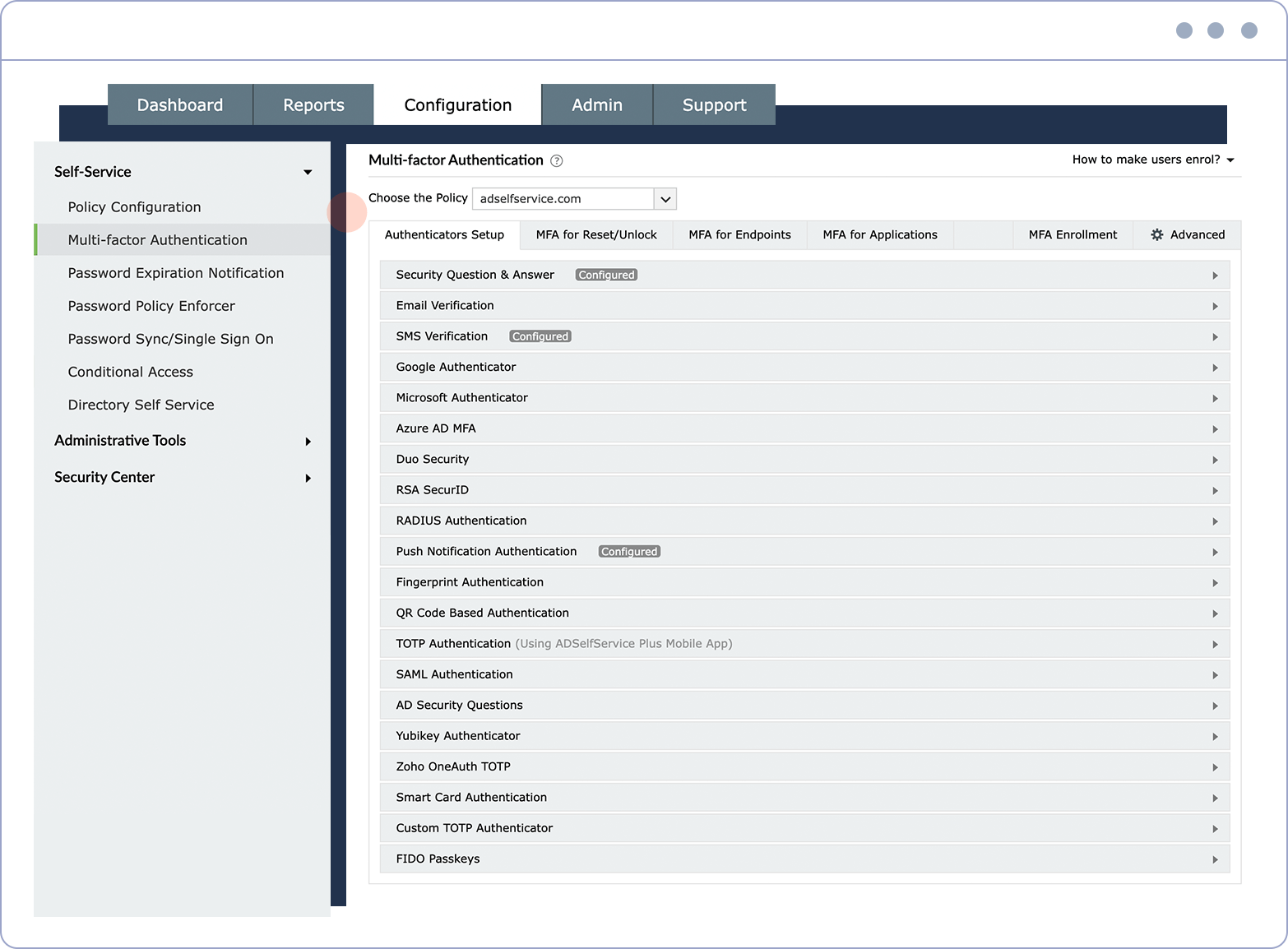
Ample authenticators Choose from around 20 different authenticators to verify your users' identities.
Implement context-based MFA for users logging in to endpoints; cloud and on-premises applications; VPNs; and OWAs.
Deploy an MFA solution that utilizes existing identity verification sources such as Face ID, Google Authenticator, or Azure AD MFA to make user adoption simple.
Render compromised passwords powerless with a secondary factor of authentication. Enable passwordless authentication and get rid of all your password management troubles at once.
Make your organization meet various compliance standards including NIST SP 800-63B, PCI DSS, and HIPAA.
Allow users to access all enterprise applications with a single, secure authentication flow.
Learn moreEnhance remote work with cached credential updates, secure logins, and mobile password management.
Learn moreSimplify password management with self-service password resets and account unlocks, strong password policies, and password expiry notifications.
Learn moreDelegate profile updates and group subscriptions to end users and monitor these self-service actions with approval workflows.
Learn moreEstablish an efficient and secure IT environment through integration with SIEM, ITSM, and IAM tools.
Learn moreCreate a Zero Trust environment with advanced identity verification techniques and render your networks impenetrable to threats.
Learn more